Environment
Identity Manager 4.x
Situation
By default the certificates created by the eDir-to-eDir Driver Certificates wizard used to secure the eDirectory to eDirectory driver expire after 2 years. Sometimes when running the eDir-to-eDir Driver Certificates wizard, the certificate creation can fail for various reasons.
How can you secure the eDirectory to eDirectory driver connection manually with KMO's using iManager?
How can you secure the eDirectory to eDirectory driver connection manually with KMO's using iManager?
Resolution
1. Login to iManager on the First Tree.
2. Create a Server Certificate for your server running the eDirectory Driver in the First Tree.
- iManager, NetIQ Certificate Server role, Create Server Certificate task.
- Select the IDM server running your eDirectory driver in the First Tree.
- Give it a nickname.
- Select Custom.
- Click Next
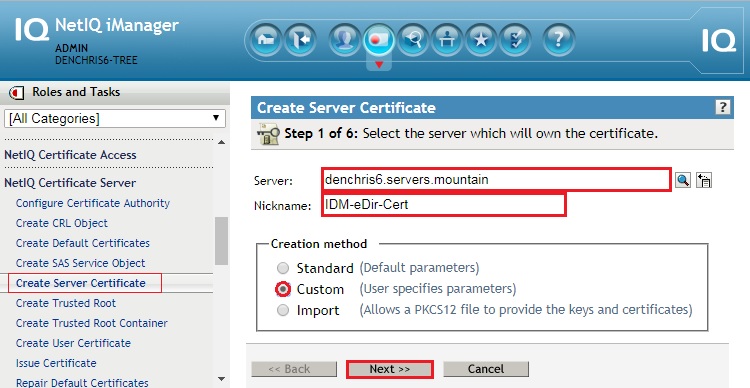
- Select Organizational certificate authority, click next
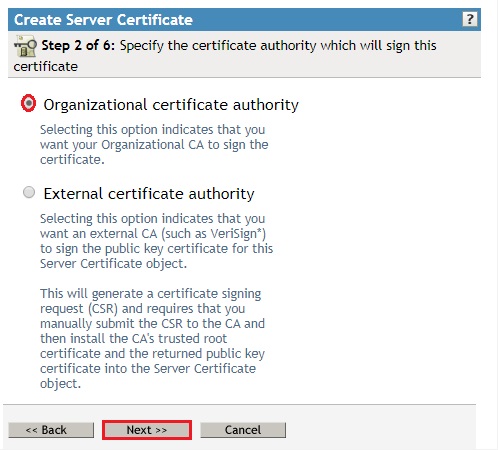
- Verify the Key size is 2048 (bits), the Key type is SSL or TLS, and that Server is selected in the Extended key type, then click Next.
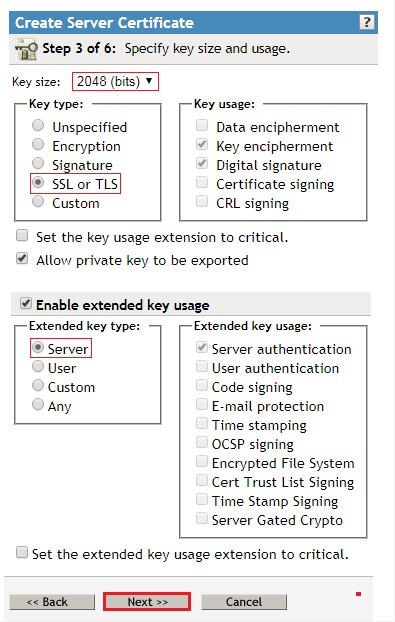
- Select SHA 256-RSA (SHA2) as the signature algorithm, and Maximum as the Validity period, and click Next.
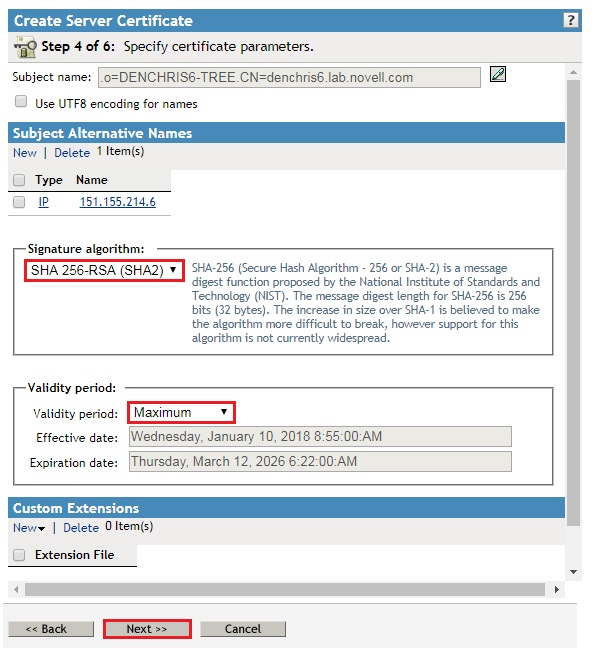
- Select Your organization's certificate and click Next.
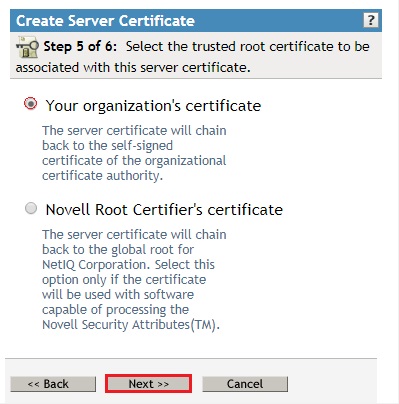
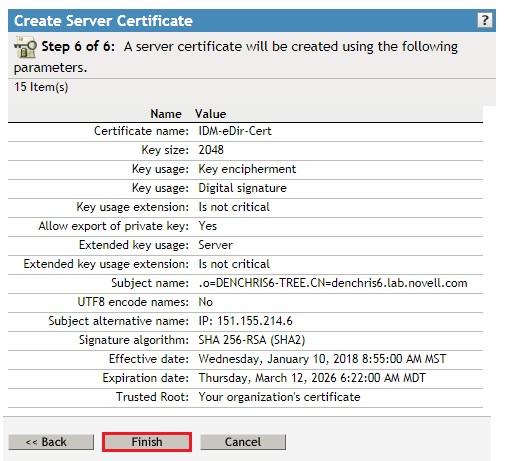
- Click Finish on the summary screen to create the certificate.
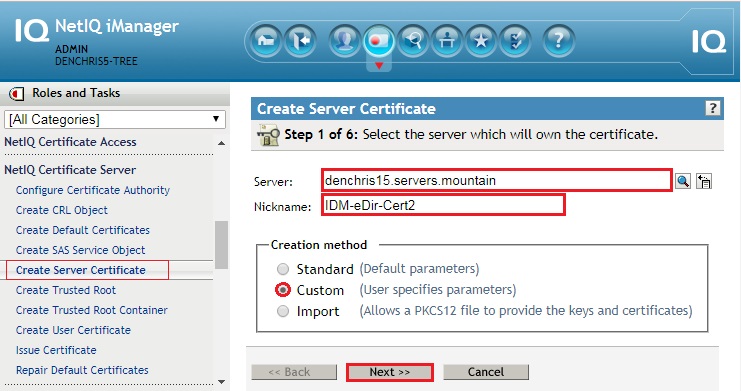
3. Login to the Second Connected Tree in iManager (other tree you are synchronizing to)
4. Create a Server Certificate for server running the eDirectory Driver in the Second Tree.
- iManager, NetIQ Certificate Server role, Create Server Certificate task.
- Select the IDM server running your eDirectory driver.
- Give it a nickname.
- Select Custom.
- Click Next
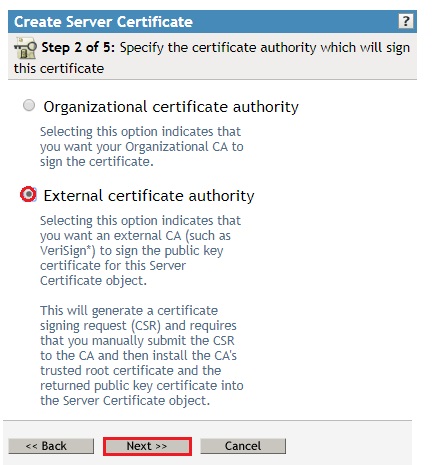
- Select External Certificate Authority and click Next.
- Select 2048 as the keysize to match the keysize that was selected on the certificate we created in the First Tree.
- Click Next
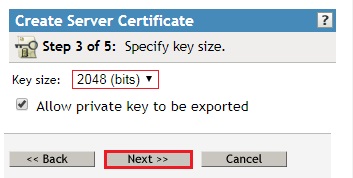
- Select SHA 256-RSA (SHA2), which is the same signature algorithm we used on the certificate in the First Tree.
- Click Next
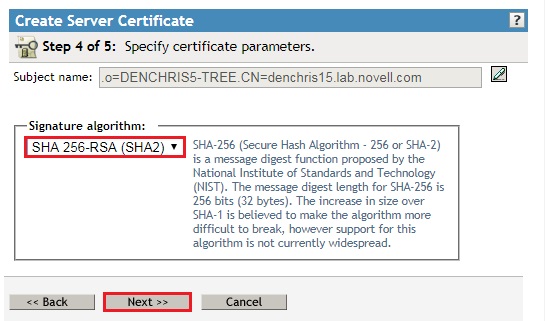
- Click Finish
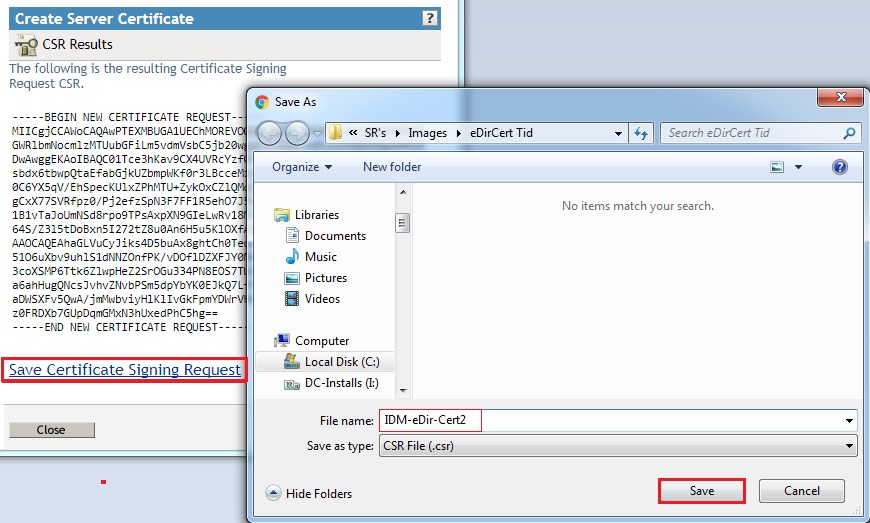
- Save the Certificate Signing Request on your workstation.
- Then click Close
5. - Logout of iManager on the Second Connected Tree and log back into iManager on the First Tree.
6. Issue a Certificate for your server running the eDirectory Driver in the first tree.
- iManager, NetIQ Certificate Server role, Issue Certificate task.
- Browse for the .csr file you saved from the server in the second connected tree.
- Click Next
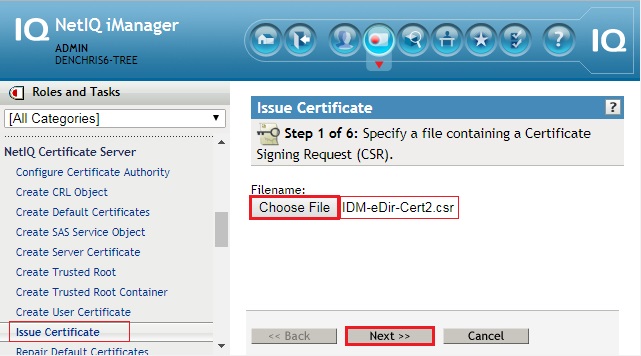
- Match the settings you selected in the original certificate in the first tree.
- Key type: SSL or TLS
- Extened key type: Server
- click Next
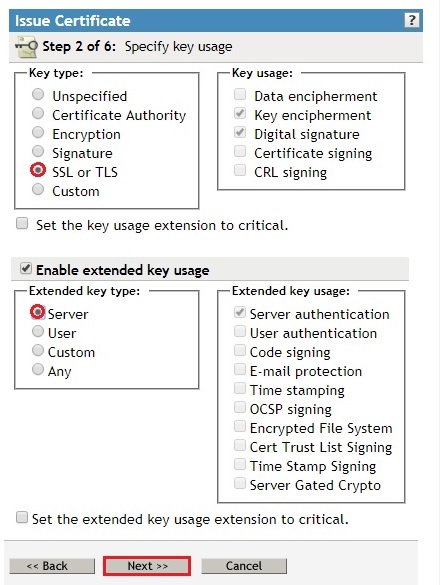
- Leave the the Certificate Type and Path length default (Unspecified) and click Next.
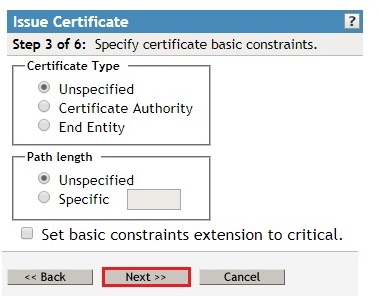
- Select Maximum on the Validity Period and click Next.
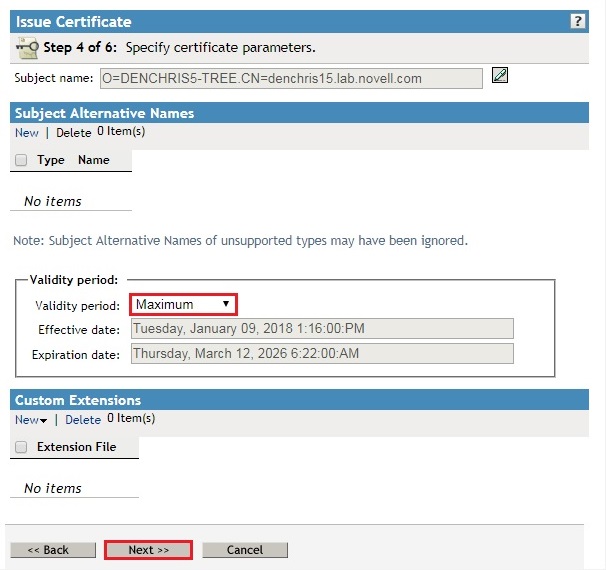
- Select Save to File in Base64 format, and click next
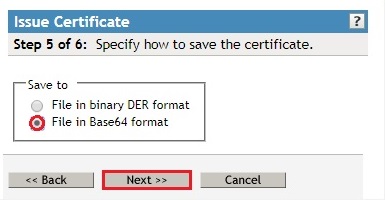
- Click Finish
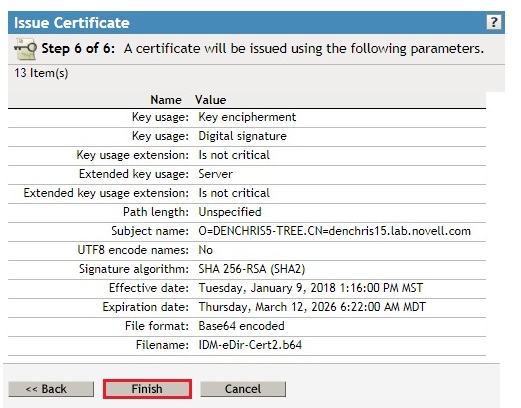
- Download the issued Certificate saving it to a file name and location of your choice, and then click Close
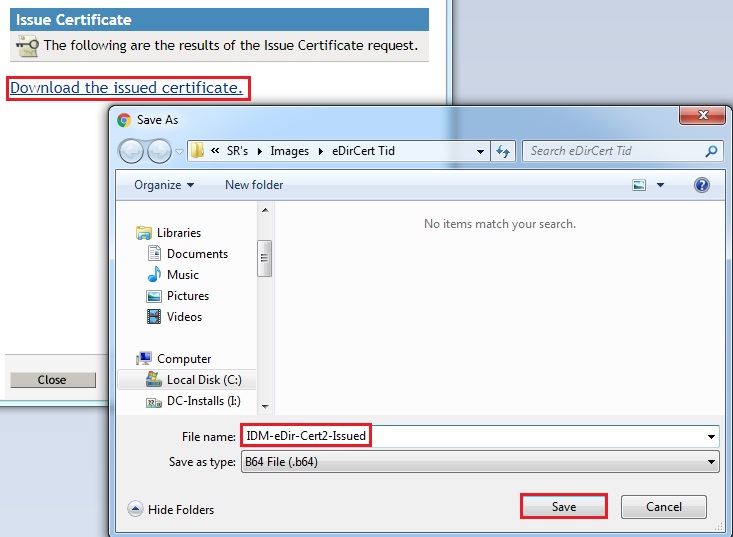
7. Export the Tree CA Self Signed Certificate from the First Tree.
8. Stay logged into iManager in the First Tree, and export the Self Signed Certificate from the Tree CA.
- iManager, NetIQ Certificate Server role, Configure Certificate Authority task.
- Select the Certificates Tab.
- Check the box next to Self Signed Certificate and click Export
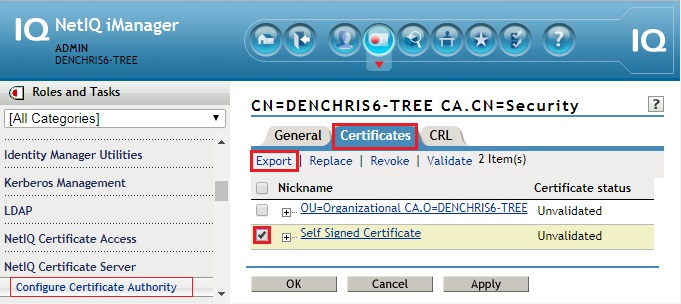
- Uncheck Export private key, select Base64 in the Export format, and click Next
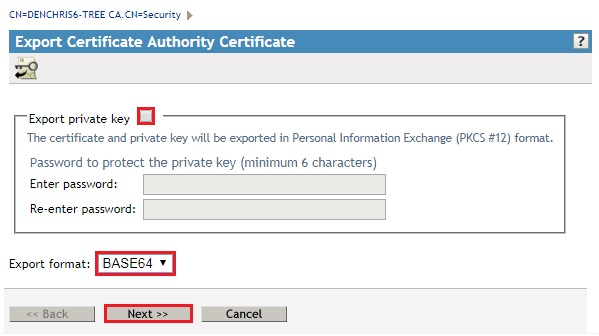
- Click Save the exported certificate, and save it to a name and location of your choice. (IDM-eDir-Tree1CA-Cert.b64)
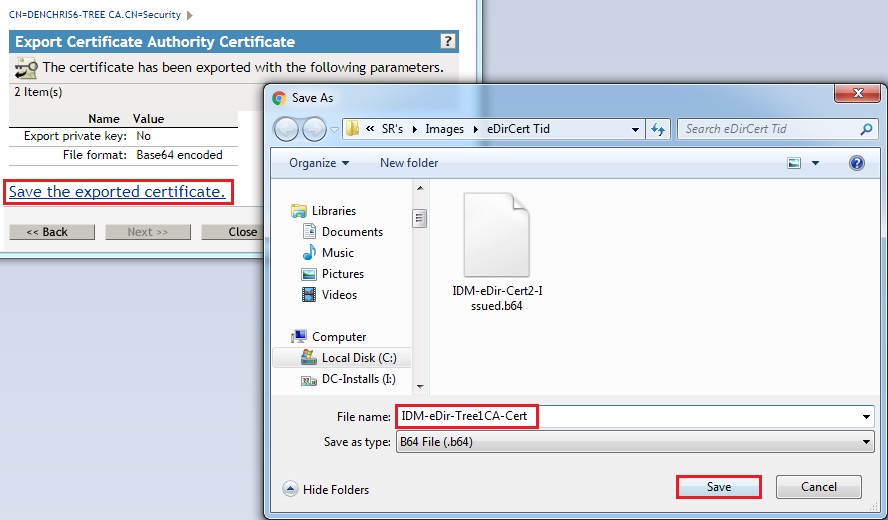
9. Login to iManager in the Second Connected tree.
10. Import the Issued Certificate from the First Tree into the Certificate you created in the Second Connected Tree.
- iManager, NetIQ Certificate Access role, Server Certificates task.
- Select the server you running the eDirectory driver on in the Second Connected Tree, (the server you selected in Step 4 above).
- The Certificate you created should show up in the list. Click Import under the Certificate status.
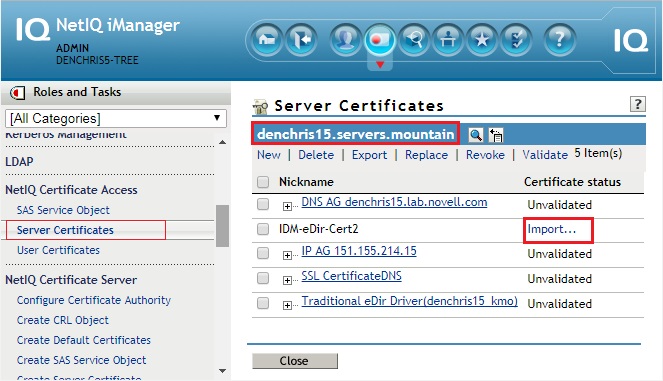
- Browse and Select the Self Signed Certificate you exported from the First Tree (IDM-eDir-Tree1-CA-Cert.b64) and click OK. (BUT DO NOT CLICK NEXT)
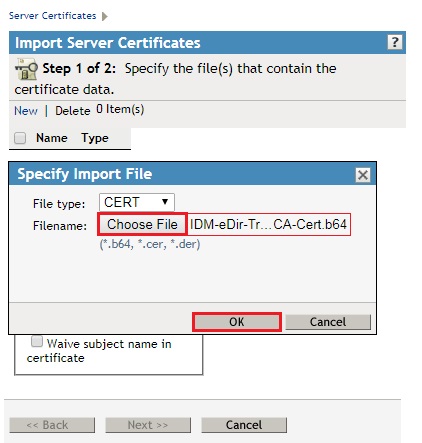
- BEFORE clicking NEXT, Click New, and Browse and Select the Signed Issued Certificate you saved from Tree1. (IDM-eDir-Tree2-Issued.b64) (Note that it has Tree2 specified on it, as the Certificate Signing Request (CSR) was originally issued from Tree2, and then signed by Tree1 and saved.) then click OK.
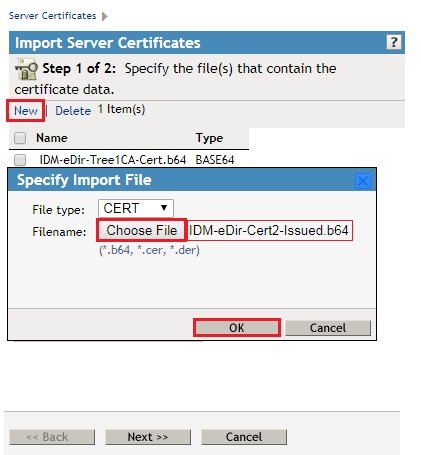
- You should now have two certificates that you are going to import. The Self Signed Tree CA certificate and the Signed Server Certificate.
- Click Next.
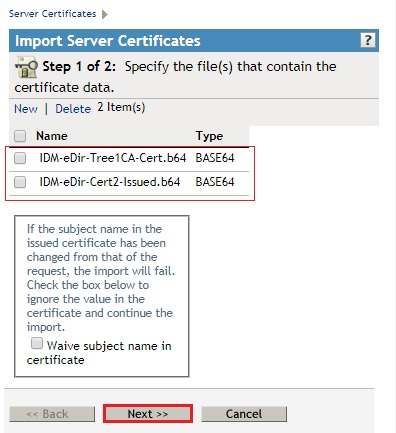
- Click Finish
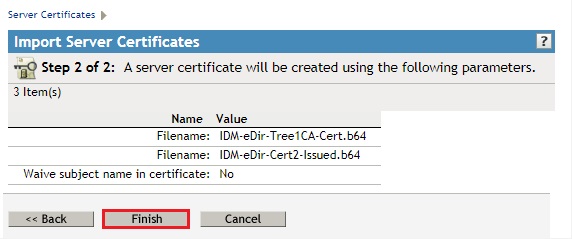
- Click Close. Note that Success is listed in the Result column.
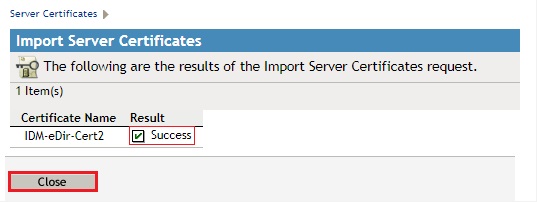
11. Configure your drivers to use the new certificates.
12. As you are already logged into iManager on the Second Connected Tree, edit the properties of the eDirectory Driver in the Second Connected Tree, and configure the driver to use the new certificate you just configured in Step 10.
- iManager, Identity Manager role, Identity Manager Overview task, click on your driver set, edit the properties of your eDirectory driver.
- Select the Identity Manager tab, Driver Configuration sub-tab and scroll down to the Driver Parameters section. Make sure that KMO is listed under Driver Settings, SSL type.
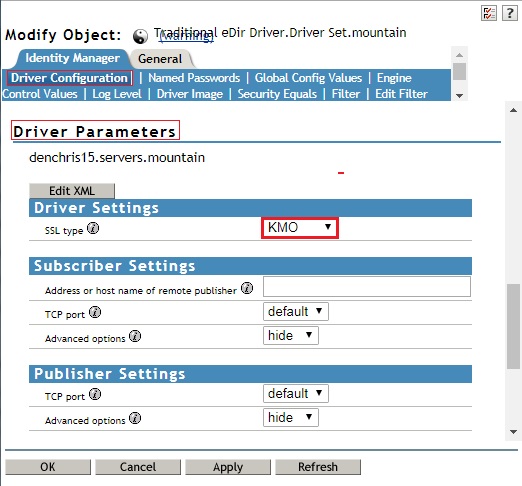
- Then scroll up under the Authentication section of the Driver Configuration, and specify the name of the certificate you created in this tree, the Second Connected Tree. (IDM-eDir-Cert2).
- Click OK to save, and restart the driver.
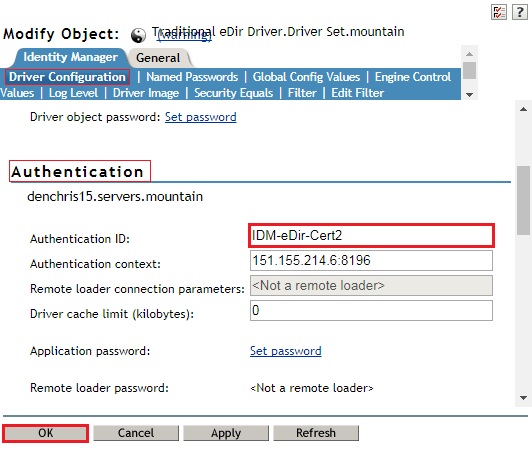
13. Login to iManager on the First Tree, edit the properties of the eDirectory Driver in the First Tree, and configure the driver to use the new certificate you just configured in Step 1.
- iManager, Identity Manager role, Identity Manager Overview task, click on your driver set, edit the properties of your eDirectory driver.
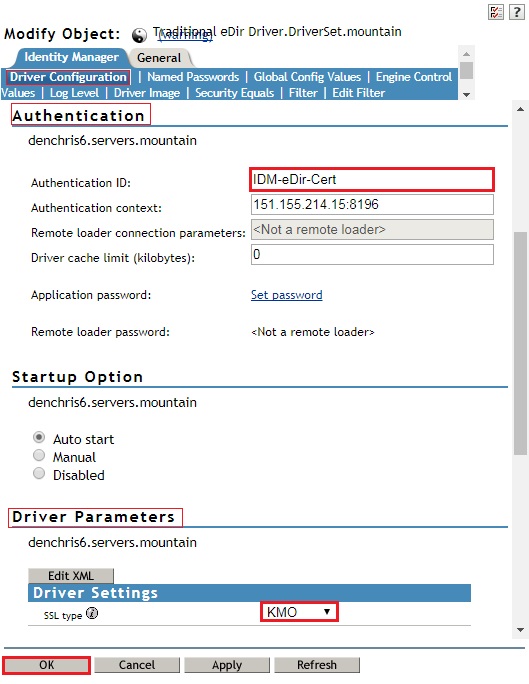
- Select the Identity Manager tab, Driver Configuration sub-tab and scroll down to the Driver Parameters section and make sure that KMO is specified under Driver Settings, SSL type.
- Then specify the Certificate you created in step 1, in Authentication ID field under the Authentication section. (IDM-eDir-Cert)
- Click OK to save and restart the driver.
14. The driver connection should now be secured using the new certificates you manually created. Test synchronization and verify it is working by modifying some objects and see if the attributes sync to and from the connected tree.
If there are any problems, troubleshoot the issue by turning the driver logs to level 3 and review the log files.
If you do have problems, one possible test is to remove the certificates from the Authentication ID field in both drivers and see if the drivers will synchronize a simple attribute like description. You can synchronize attributes (but not passwords) over a non-secure connection. If the driver will not synchronize description on a non-secure connection, then there is some other issue with the driver synchronization which will have resolved before you can attempt to secure the driver synchronization.
2. Create a Server Certificate for your server running the eDirectory Driver in the First Tree.
- iManager, NetIQ Certificate Server role, Create Server Certificate task.
- Select the IDM server running your eDirectory driver in the First Tree.
- Give it a nickname.
- Select Custom.
- Click Next

- Select Organizational certificate authority, click next

- Verify the Key size is 2048 (bits), the Key type is SSL or TLS, and that Server is selected in the Extended key type, then click Next.

- Select SHA 256-RSA (SHA2) as the signature algorithm, and Maximum as the Validity period, and click Next.

- Select Your organization's certificate and click Next.

- Click Finish on the summary screen to create the certificate.

3. Login to the Second Connected Tree in iManager (other tree you are synchronizing to)
4. Create a Server Certificate for server running the eDirectory Driver in the Second Tree.
- iManager, NetIQ Certificate Server role, Create Server Certificate task.
- Select the IDM server running your eDirectory driver.
- Give it a nickname.
- Select Custom.
- Click Next

- Select External Certificate Authority and click Next.

- Select 2048 as the keysize to match the keysize that was selected on the certificate we created in the First Tree.
- Click Next

- Select SHA 256-RSA (SHA2), which is the same signature algorithm we used on the certificate in the First Tree.
- Click Next

- Click Finish

- Save the Certificate Signing Request on your workstation.
- Then click Close

5. - Logout of iManager on the Second Connected Tree and log back into iManager on the First Tree.
6. Issue a Certificate for your server running the eDirectory Driver in the first tree.
- iManager, NetIQ Certificate Server role, Issue Certificate task.
- Browse for the .csr file you saved from the server in the second connected tree.
- Click Next

- Match the settings you selected in the original certificate in the first tree.
- Key type: SSL or TLS
- Extened key type: Server
- click Next

- Leave the the Certificate Type and Path length default (Unspecified) and click Next.

- Select Maximum on the Validity Period and click Next.

- Select Save to File in Base64 format, and click next

- Click Finish

- Download the issued Certificate saving it to a file name and location of your choice, and then click Close

7. Export the Tree CA Self Signed Certificate from the First Tree.
8. Stay logged into iManager in the First Tree, and export the Self Signed Certificate from the Tree CA.
- iManager, NetIQ Certificate Server role, Configure Certificate Authority task.
- Select the Certificates Tab.
- Check the box next to Self Signed Certificate and click Export

- Uncheck Export private key, select Base64 in the Export format, and click Next

- Click Save the exported certificate, and save it to a name and location of your choice. (IDM-eDir-Tree1CA-Cert.b64)

9. Login to iManager in the Second Connected tree.
10. Import the Issued Certificate from the First Tree into the Certificate you created in the Second Connected Tree.
- iManager, NetIQ Certificate Access role, Server Certificates task.
- Select the server you running the eDirectory driver on in the Second Connected Tree, (the server you selected in Step 4 above).
- The Certificate you created should show up in the list. Click Import under the Certificate status.

- Browse and Select the Self Signed Certificate you exported from the First Tree (IDM-eDir-Tree1-CA-Cert.b64) and click OK. (BUT DO NOT CLICK NEXT)

- BEFORE clicking NEXT, Click New, and Browse and Select the Signed Issued Certificate you saved from Tree1. (IDM-eDir-Tree2-Issued.b64) (Note that it has Tree2 specified on it, as the Certificate Signing Request (CSR) was originally issued from Tree2, and then signed by Tree1 and saved.) then click OK.

- You should now have two certificates that you are going to import. The Self Signed Tree CA certificate and the Signed Server Certificate.
- Click Next.

- Click Finish

- Click Close. Note that Success is listed in the Result column.

11. Configure your drivers to use the new certificates.
12. As you are already logged into iManager on the Second Connected Tree, edit the properties of the eDirectory Driver in the Second Connected Tree, and configure the driver to use the new certificate you just configured in Step 10.
- iManager, Identity Manager role, Identity Manager Overview task, click on your driver set, edit the properties of your eDirectory driver.
- Select the Identity Manager tab, Driver Configuration sub-tab and scroll down to the Driver Parameters section. Make sure that KMO is listed under Driver Settings, SSL type.

- Then scroll up under the Authentication section of the Driver Configuration, and specify the name of the certificate you created in this tree, the Second Connected Tree. (IDM-eDir-Cert2).
- Click OK to save, and restart the driver.

13. Login to iManager on the First Tree, edit the properties of the eDirectory Driver in the First Tree, and configure the driver to use the new certificate you just configured in Step 1.
- iManager, Identity Manager role, Identity Manager Overview task, click on your driver set, edit the properties of your eDirectory driver.
- Select the Identity Manager tab, Driver Configuration sub-tab and scroll down to the Driver Parameters section and make sure that KMO is specified under Driver Settings, SSL type.
- Then specify the Certificate you created in step 1, in Authentication ID field under the Authentication section. (IDM-eDir-Cert)
- Click OK to save and restart the driver.

14. The driver connection should now be secured using the new certificates you manually created. Test synchronization and verify it is working by modifying some objects and see if the attributes sync to and from the connected tree.
If there are any problems, troubleshoot the issue by turning the driver logs to level 3 and review the log files.
If you do have problems, one possible test is to remove the certificates from the Authentication ID field in both drivers and see if the drivers will synchronize a simple attribute like description. You can synchronize attributes (but not passwords) over a non-secure connection. If the driver will not synchronize description on a non-secure connection, then there is some other issue with the driver synchronization which will have resolved before you can attempt to secure the driver synchronization.
Additional Information
Link to Youtube video on how to secure the eDirectory Driver using KMO's & iManager.
https://www.youtube.com/watch?v=7L1jbGmgZiM&t=244s
TID 3578820 - Manually Creating NDS-to-NDS eDirectory Driver Certificates with ConsoleOne
TID 7011721 - Using a Java keystore file to secure the eDir to eDir Driver Connection
https://www.youtube.com/watch?v=7L1jbGmgZiM&t=244s
TID 3578820 - Manually Creating NDS-to-NDS eDirectory Driver Certificates with ConsoleOne
TID 7011721 - Using a Java keystore file to secure the eDir to eDir Driver Connection