Environment
Novell eDirectory 8.7.3 SP9 FTF2 for All Platforms
Novell eDirectory 8.8 SP2 for All Platforms
Situation
High utilization, unresponsiveness, and/or client timeouts can be symptoms of busy authentication servers. These symptoms can often be the result of eDirectory modifying or updating user objects login attributes after they have logged in.
These Login Attributes include:
Login Time
Network Address
Last Login Time
Revision
etc.
If thousands of logins are occurring in a short amount of time, during peak login times, long lock times (unresponsiveness) may result when eDirectory writes these changes to the database.
(Please see KB 3812871 for information on how to identify and troubleshoot eDirectory database locks.)
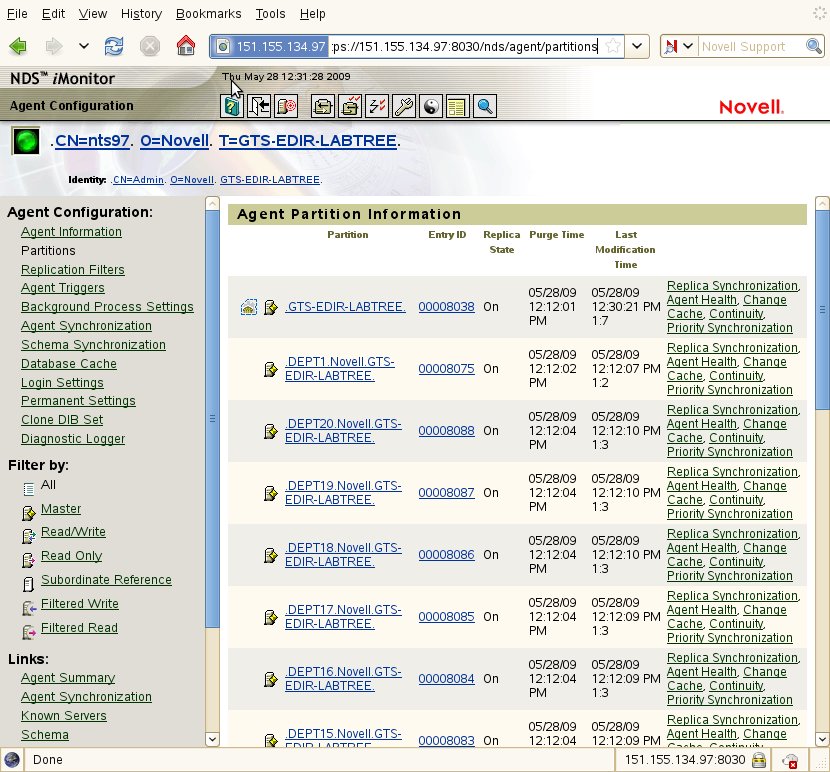
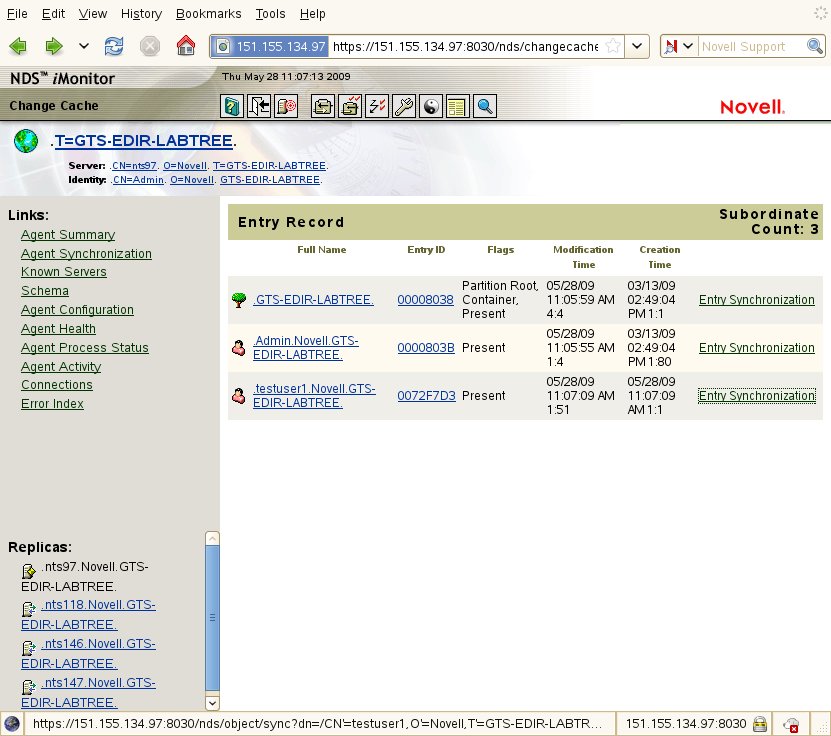
To verify these symptoms are releated to updating login atributes, start by viewing the user partition's Entry Cache in iMonitor. If there are hundreds of user objects in change cache and if their modified values are associated to login attributes then this could be the case.
Once logged into to iMonitor (https://xxx.xxx.xxx.xxx:8030/nds) Select Agent Configuration | Partitions | then select the "Change Cache" link next to the desired partition.
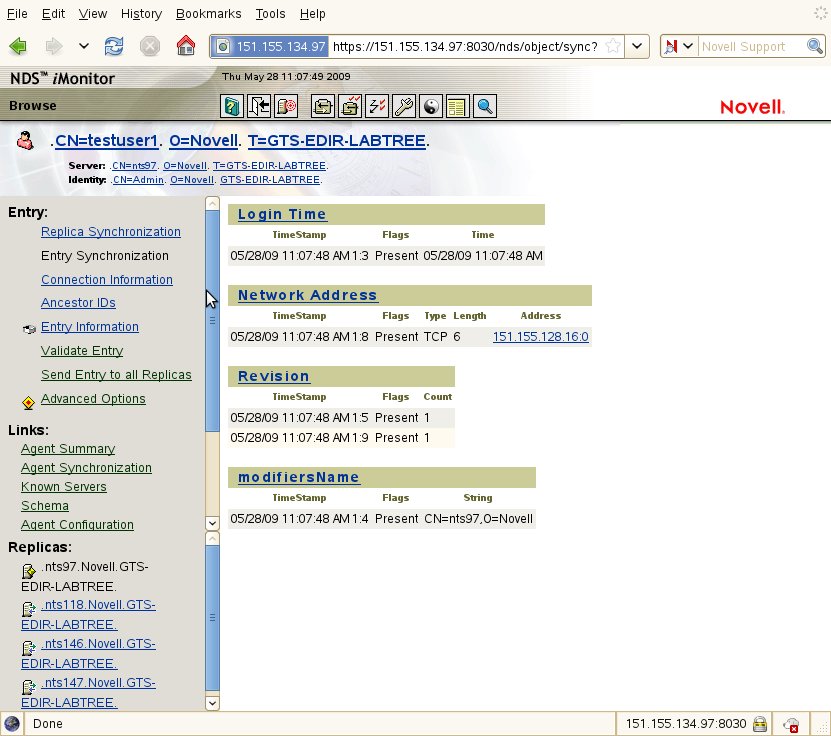
Clicking on the objects "Entry Synchronization" link will show which attributes have recently been modified and are the cause of this entry being added to the change cache.
Shown below, we see the attributes (Login Time, Network Address, Revision, modifiersName) in change cache. These attributes are related to updating the login attributes for that user.
Not only will these "Login update" changes ultimately be written to the database, however they must also be synchronized to all other servers in the replica ring and those servers must also write the changes to their database.
Resolution
In the past, the way to eliminate this from happening was to simply disable the login update via iMonitor. The drawback was that the Intruder Detection would no longer work since it relies on the Login Intruder Attempts attribute to be updated.
Beginning with eDirectory 8.7.3.9FTF2 and eDirectory 8.8 SP2, updating of login attributes can be disabled while preserving the functionality of detecting intruders and locking an account after a certain number of failed authentications. The following changes must be disabled on all authentication servers. Below is the procedure:
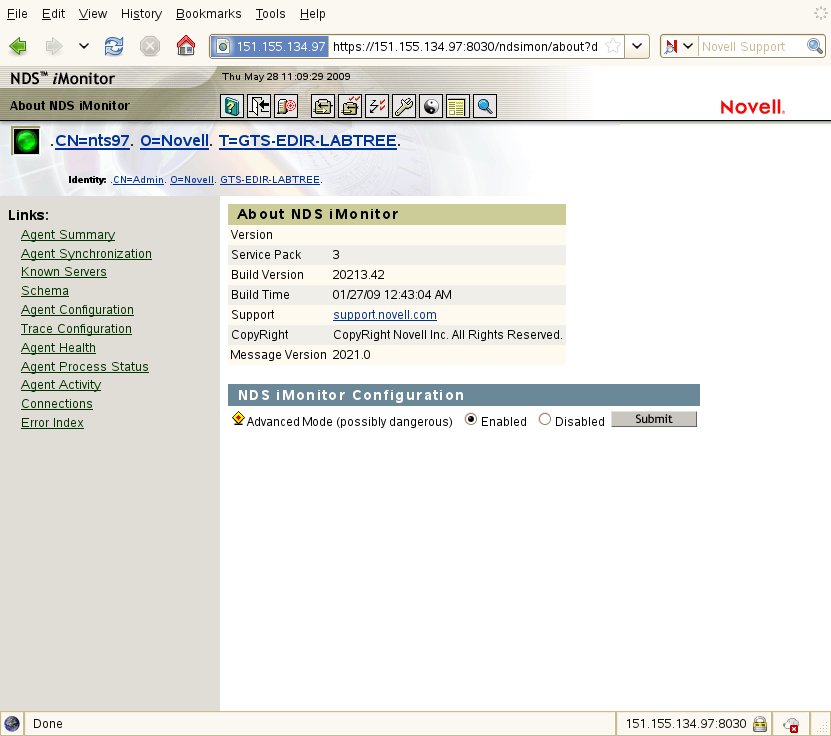
1. Login to iMonitor and turn on the Advanced Mode by clicking on the iMonitor logo in the upper left corner of the screen.
2. Next go to Agent Configuration | Permanent Settings | Change.
3. Using the drop down selector, select the Disable Attribute Update and change the Value to "1" (one.)
4. Select Save and this server's configuration is complete. Remember to do this for all main authentication servers.
Note: Leave the other fields at their defaults as they are not applicable to this permanent setting.
Note: Leave the other fields at their defaults as they are not applicable to this permanent setting.
Local Only: Unchecked - setting is written to both the pseudoserver and the ncp server object
Preserve TTL: Unchecked - this setting will not expire when the time specified in the TTL fields is reached
Status
Top IssueAdditional Information
NMAS Information:
Though the above steps will stop login updates from occurring on user objects if they are using NDS passwords while maintaining intruder detection. NMAS will also update these attributes if Universal Password is enabled.
This can be turned off as well when using NMAS 3.2 as it shipped with eDirectory 8.8.2, OES 2, NetWare 6.5 SP7 and Security Services 2.0.5. by executing the command " nmas LoginInfo (num) ".
The value for (num) is as follows:
0 or off = do not update any login attributes
1 = only update attributes required by intruder detection
2 = update all login attributes except unused user password policy attributes
3 or on = update all login attributes
Below are the steps to implement the login update behavior on each platform.
NetWare: The command can be added near the end of the autoexec.ncf. The command can also be executed at the NetWare console.
Windows: When NMAS is started, it processes the commands in the file nmas.cfg . The nmas.cfg file must be in the same directory as the dib files which is usually c:/novell/nds/dibfiles. This command can also be executed
from the Novell® eDirectoryTM Services console by selecting nmas.dlm, typing the command in the Startup Parameters field, then clicking Configure. Note that the content to be included in the file is only "nmas LoginInfo <num>".
Linux/Solaris/AIX/HPUX:
from the Novell® eDirectoryTM Services console by selecting nmas.dlm, typing the command in the Startup Parameters field, then clicking Configure. Note that the content to be included in the file is only "nmas LoginInfo <num>".
Linux/Solaris/AIX/HPUX:
When NMAS is started, it processes the commands in the file nmas.config. The nmas.config file must be in the same directory as the data directory. The dib directory is usually an immediate subordinate of the data directory.
For example, if the dib directory path is "/var/opt/novell/eDirectory/data/dib" then the nmas.config file path would be "/var/opt/novell/eDirectory/data/nmas.config" File permissions on this file should be set to at least 644. Nmas uses the same uid that ndsd uses so the owner should be root, unless it is a non root install. Then of course the owner should be the same user/uid that is running ndsd. Note that the content to be included in the file is only "nmas LoginInfo <num>".
Attributes that get updated at each login info level
---------------------------------------------------------------------------------------------------
sasUpdateLoginInfo = 1 (Only update intruder detection attributes and not other login attributes)
---------------------------------------------------------------------------------------------------
1) Intruder Attributes:
On Failure: Login Intruder Attempts
Locked By Intruder
Login Intruder Reset Time
pwdAccountLockedTime
Login Intruder Address
On Success: Login Intruder Attempts
Locked By Intruder
Login Intruder Reset Time
pwdAccountLockedTime
-----------------------------------------------------------------------------------------
sasUpdateLoginInfo = 2 (Update only login attributes and not password policy attributes)
-----------------------------------------------------------------------------------------
1) Attributes at level 1 (Intruder attributes)
+
2) Login Attributes:
On Failure: pwdFailureTime
On Success: Login Time
Last Login Time
pwdFailureTime
Login Grace Remaining (if request sent)
----------------------------------------------------------------------------
sasUpdateLoginInfo = 3 (Update login 'and' user password policy attributes)
----------------------------------------------------------------------------
1) Attributes at level 2 (Intruder + Login Attributes)
+
2) Password Policy Attributes:
Password Required
Password Expiration Interval
Password Expiration Time
Login Grace Limit
Login Grace Remaining
Password Allow Change
Password Minimum Length
Password Unique Required
For example, if the dib directory path is "/var/opt/novell/eDirectory/data/dib" then the nmas.config file path would be "/var/opt/novell/eDirectory/data/nmas.config" File permissions on this file should be set to at least 644. Nmas uses the same uid that ndsd uses so the owner should be root, unless it is a non root install. Then of course the owner should be the same user/uid that is running ndsd. Note that the content to be included in the file is only "nmas LoginInfo <num>".
Attributes that get updated at each login info level
---------------------------------------------------------------------------------------------------
sasUpdateLoginInfo = 1 (Only update intruder detection attributes and not other login attributes)
---------------------------------------------------------------------------------------------------
1) Intruder Attributes:
On Failure: Login Intruder Attempts
Locked By Intruder
Login Intruder Reset Time
pwdAccountLockedTime
Login Intruder Address
On Success: Login Intruder Attempts
Locked By Intruder
Login Intruder Reset Time
pwdAccountLockedTime
-----------------------------------------------------------------------------------------
sasUpdateLoginInfo = 2 (Update only login attributes and not password policy attributes)
-----------------------------------------------------------------------------------------
1) Attributes at level 1 (Intruder attributes)
+
2) Login Attributes:
On Failure: pwdFailureTime
On Success: Login Time
Last Login Time
pwdFailureTime
Login Grace Remaining (if request sent)
----------------------------------------------------------------------------
sasUpdateLoginInfo = 3 (Update login 'and' user password policy attributes)
----------------------------------------------------------------------------
1) Attributes at level 2 (Intruder + Login Attributes)
+
2) Password Policy Attributes:
Password Required
Password Expiration Interval
Password Expiration Time
Login Grace Limit
Login Grace Remaining
Password Allow Change
Password Minimum Length
Password Unique Required
Change Log
5/28/09 - bberger - updated screenshots. Orginal screenshots were too big and included personal bookmarks.
08/20/09 - hvaughan - change title and prepare for new enhancement text.
08/24/09 - hjaitly - The nmas.config file content is only "nmas LoginInfo <num>".
08/24/09 - hjaitly - The nmas.config file content is only "nmas LoginInfo <num>".