Summary
Question
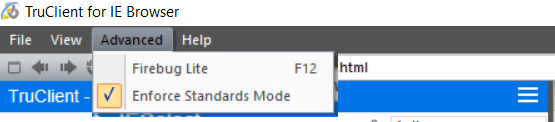
If unchecking âEnforce standard modeâ in Truclient IE can resolve the unexpected behavior, then please try this solution.
Background
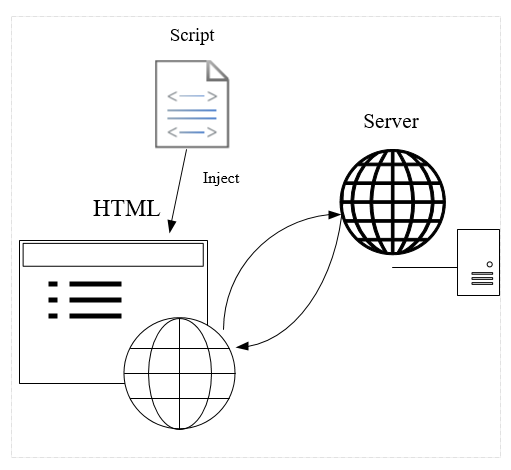
Truclient will inject code into webpages. This may cause some unexpected behavior of AUT(Application under test)
Answer
Put a âIEInjectionBlacklist.iniâ file under the script folder. To blacklist the code injection to target URLs.
Example of âIEInjectionBlacklist.iniâ format:
Example 1, use both urls and regex:
[Urls]
http://kalimanjaro.hpeswlab.net/webgui/multiplefileform.html
[http://www.google.co.il*]www.google.co.il*
http://16.44.49.218/*/Index.htm
[regexUrls]
^http:\/\/www/\.hpe/\.com\/.*
Example 2, use url only:
[Urls]
http://kalimanjaro.hpeswlab.net/webgui/multiplefileform.html
Example 3, use regex only:
[regexUrls]
^http:\/\/www/\.hpe/\.com\/.*
How do I know whether I successfully blocked code injection to the target page?
The following code will exist to page that is been injected our code:
<!doctype html><meta id="hp_injected_meta" http-equiv="X-UA-Compatible" content="IE=edge"> <script type="text/javascript" id="hp_injected_script" src="C:\Program Files (x86)\Micro Focus\LoadRunner\dat\WebIE\RRE\content\injectedCode\injectToAUTWin.js?mode=interactive"></script><!DOCTYPE html>
If you right click the page and click on âView Sourceâ, but no such signature looks like above exist. Then the blacklist should doing its job.