Environment
GWAVA (Secure Messaging Gateway) 7
SMG-on-SLES appliance
Situation
How to configure a SMG server to handle outbound messages and block inbound messages
Resolution
When creating the policies for this outbound message SMG server, one
should carefully specify the criteria so that the correct policy can
be identified and applied to scan any message that needs scanning.
The policy to be applied to outbound mail is different from the policy to be applied to inbound mail. One may choose to skip spam checks on outbound mail but add a message signature and a DKIM signature.
For occasional inbound mail that is offered on this outbound message SMG,
the policy may be set up to always block messages, but to scan and track for
statistical purposes.
We'll explain with an example.
In our example we do not define a Relay Module:
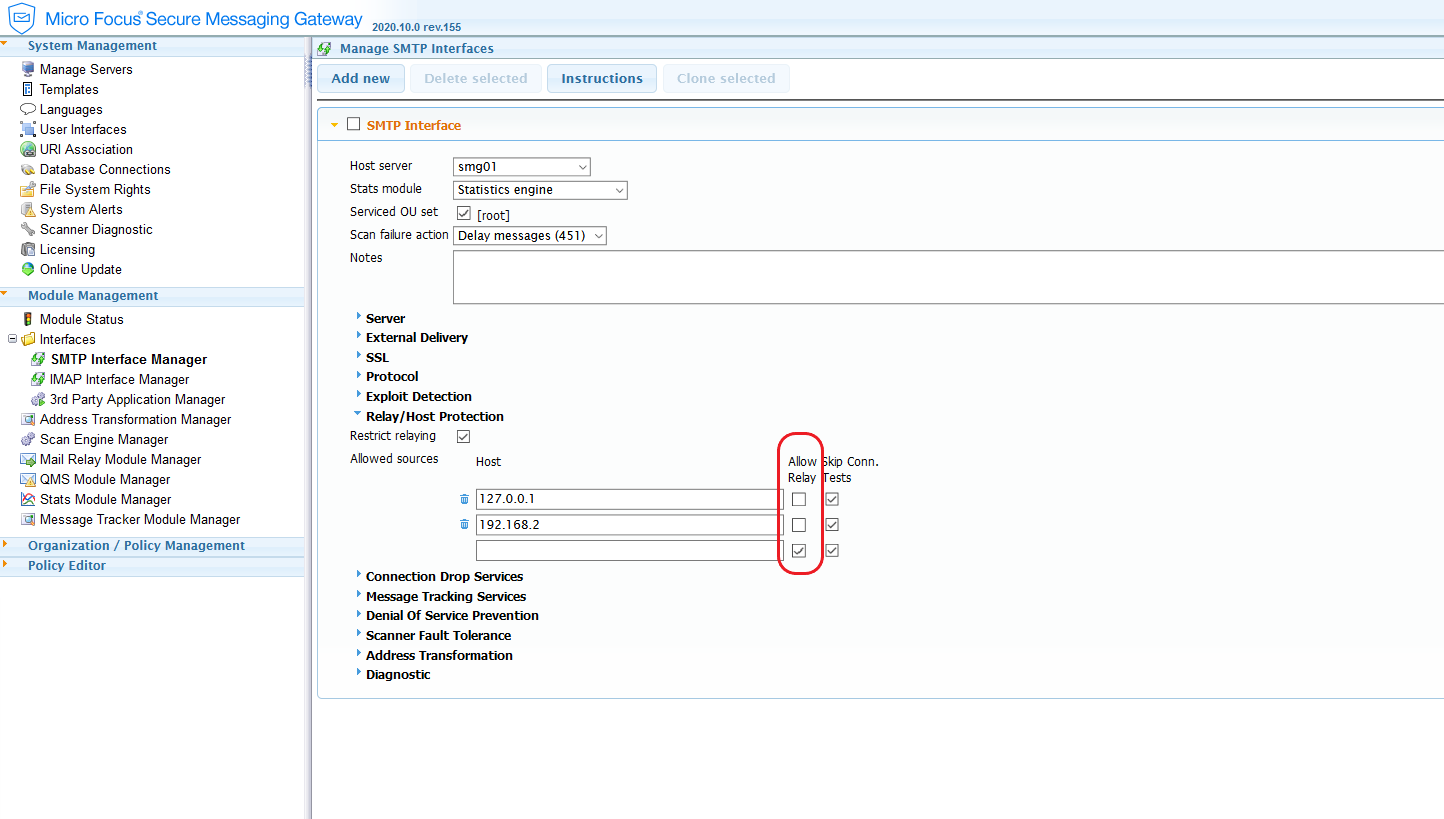
Also we do not enable relaying on the SMTP interface. This done by not checking the âAllow relayâ box on the SMTP Interface | Relay/Host Protection
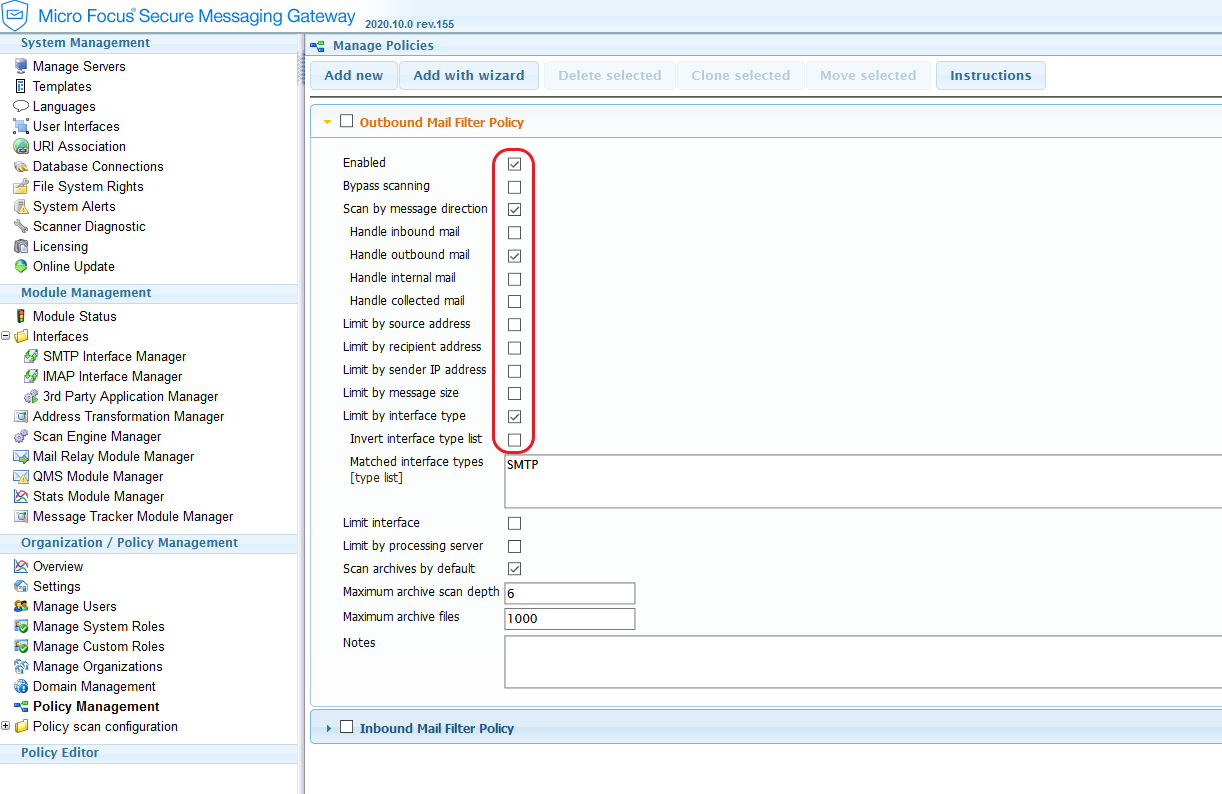
We
have configured an outbound policy, that is enabled to handle outbound message
And
configured an inbound policy that is enabled to handle occasional inbound messages
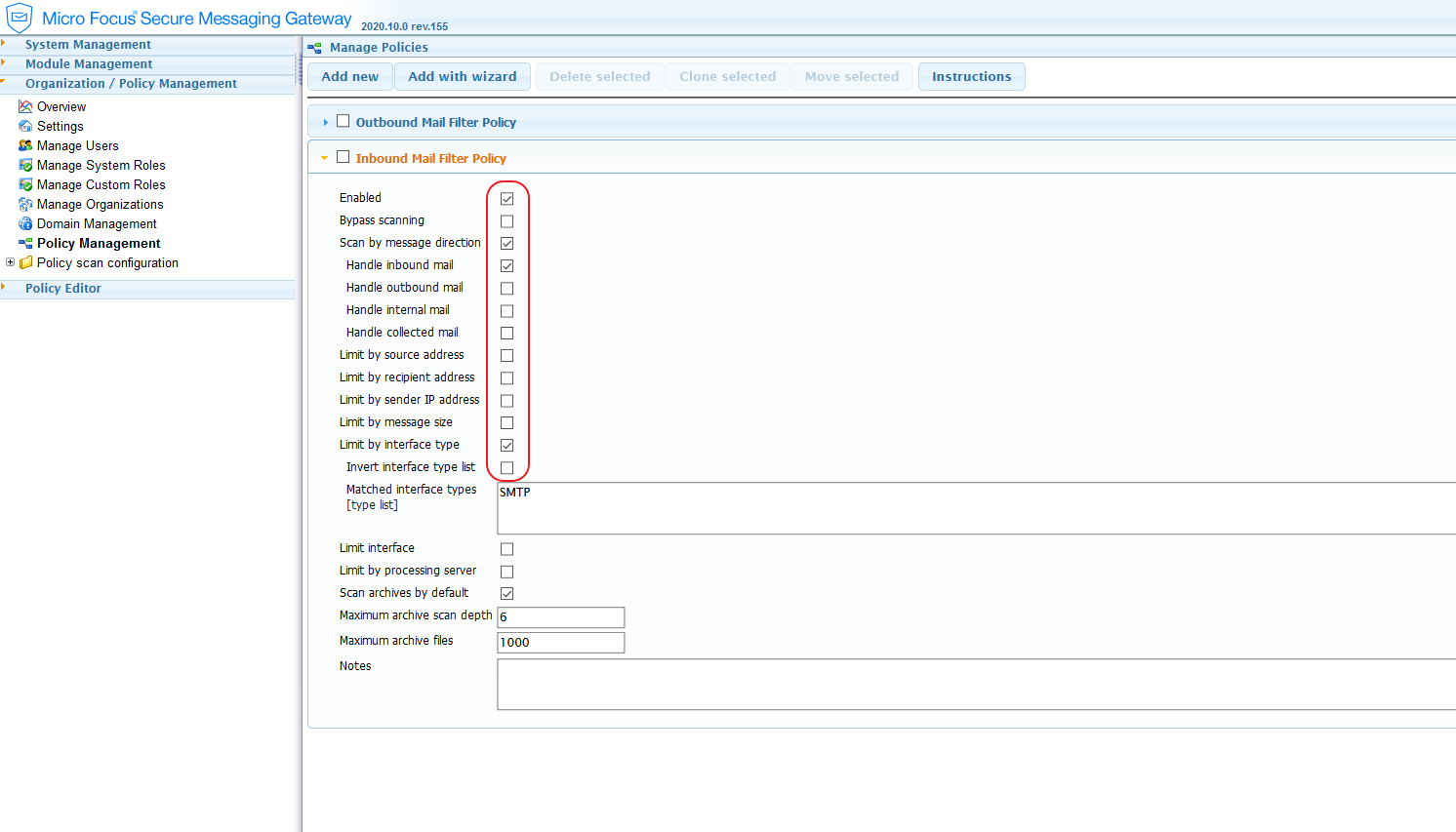
In the inbound message policy â editor, we have configured the filters as such that all inbound messages are blocked and scanned:
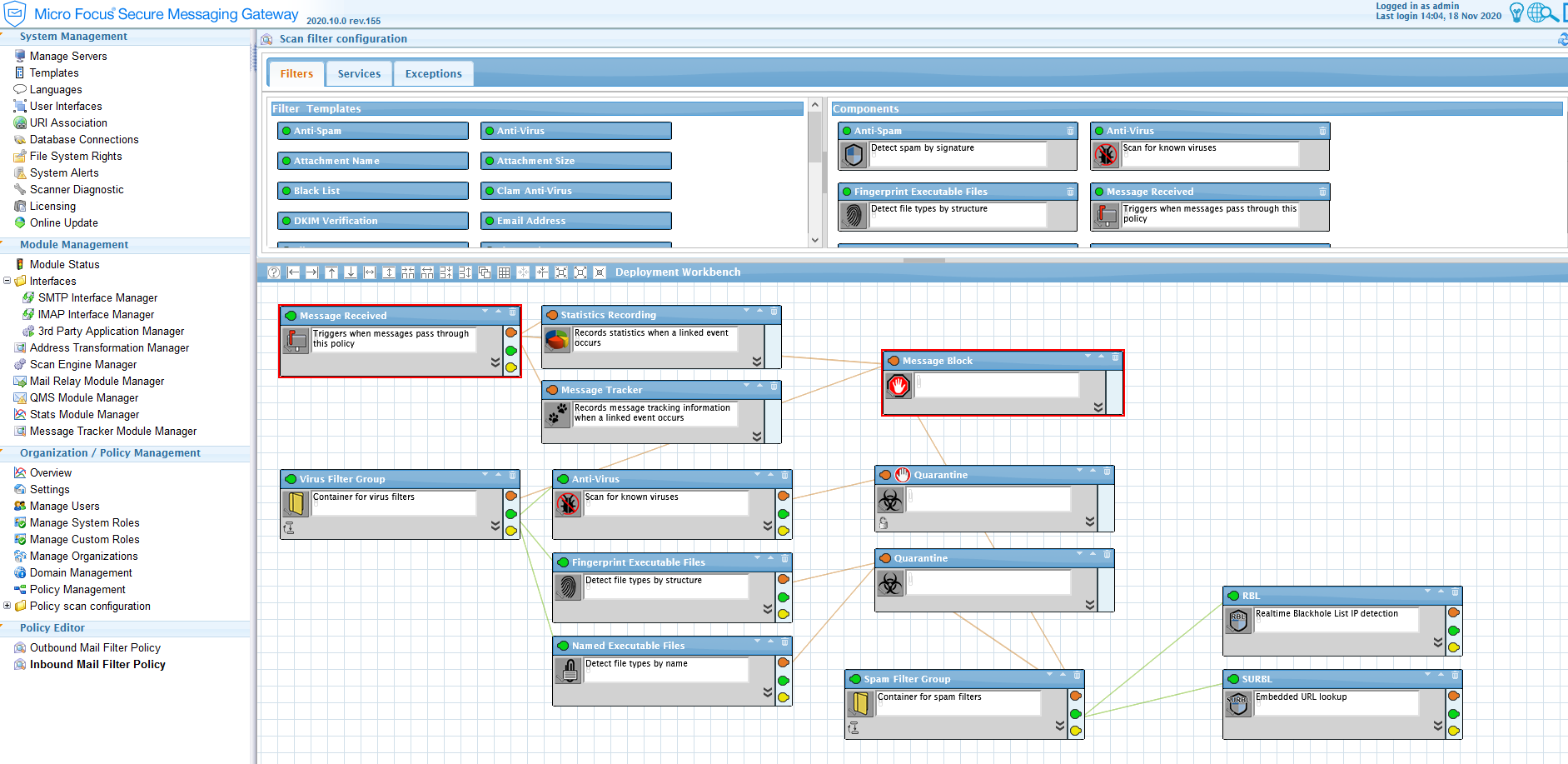
When we search in the message tracker for inbound messages, these will have been blocked by the âMessage Receivedâ filter, and occasionally also by the other filters, such as the âFinger Executable Filesâ or âVirus Filter Groupâ.
When considering
the options in the policy criteria one will recognize how to create policies
that match the specific requirements of your users. The SMG scanning policies
can be very flexible and powerful however careful consideration must be used to
craft the policies that meet the needs.
Additional Information
Keywords
SMG, SMG on SLES, mail policy, inbound, outbound