Environment
Self Service Password Reset 4.4
Self Service Password Reset 4.3
Self Service Password Reset 4.2
Situation
SSPR server configured to send Token via email to user.
Email is received by the user but when they click the link in the email or attempt to enter the token manually with copy and paste, the SSPR server returns an error "Incorrect code, please try again."
Error: 5037 ERROR_TOKEN_INCORRECT (token not found)
Resolution
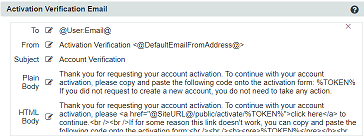
Either configure the email scanner to not process emails from the SSPR server or edit the email template in the SSPR server configuration to not include a link. (Settings ⨠Email ⨠Email Templates)
(Note that to make modifications to the email template it is recommended that you use a modern browser. For example Chrome, Firefox, Edge, etc.)
Select the email template to be modified. In this example we edit the Activation Verification Email template. Click on the notepad and pencil icon
next to the text "HTML Body".
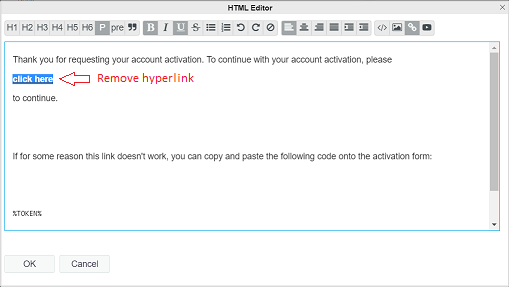
Highlight the link "click here" and then click the hyperlink icon in the toolbar
to remove the hyperlink.
Cause
Customer environment contains an outbound email scanner. The email scanner processes the link within the email sent to the user causing the token to be claimed and deleted by the server. Once the user receives the email, the issued token is no longer available and when processed will return the error.
Additional Information
SSPR server debug logs showed that the token was attempted to be claimed twice. The first claim would succeed but the subsequent attempt would fail with and error indicating that the token could not be found.
First token claim:
http.PwmRequest {390782} GET request for: /sspr/public/activate requestID=2133824 [192.168.1.200]
token.TokenService {390782} retrieved tokenPayload: {"issueTime":"2020-01-31T18:06:38Z","name":"ACTIVATION","guid":"0364437a-9999-4849-8245-750062dd1383","expiration":"2020-01-31T18:11:38Z","user":"cn=TestUser,ou=users,o=data (default)"} [192.168.1.200]
operations.PasswordUtility {390782} read last user password change timestamp (via chai) as: 2020-01-30T02:54:48Z [192.168.1.200]
token.TokenService {390782} tokenPayload={"issueTime":"2020-01-31T18:06:38Z","name":"ACTIVATION","guid":"0364437a-9999-4849-8245-750062dd1383","expiration":"2020-01-31T18:11:38Z","user":"cn=TestUser,ou=users,o=data (default)"}, sessionUser=null, payloadUserIdentity=cn=TestUser,ou=users,o=data (default), userLastPasswordChange=2020-01-30T02:54:48Z, dateStringInToken=2020-01-30T02:54:48Z [192.168.1.200]
token.TokenService {390782} token validation has been passed [192.168.1.200]
token.TokenService {390782} removing claimed token: {"issueTime":"2020-01-31T18:06:38Z","name":"ACTIVATION","guid":"0364437a-9999-4849-8245-750062dd1383","expiration":"2020-01-31T18:11:38Z","user":"cn=TestUser,ou=users,o=data (default)"} [192.168.1.200]
http.PwmRequest {390782} GET request for: /sspr/public/activate requestID=2133824 [192.168.1.200]
token.TokenService {390782} retrieved tokenPayload: {"issueTime":"2020-01-31T18:06:38Z","name":"ACTIVATION","guid":"0364437a-9999-4849-8245-750062dd1383","expiration":"2020-01-31T18:11:38Z","user":"cn=TestUser,ou=users,o=data (default)"} [192.168.1.200]
operations.PasswordUtility {390782} read last user password change timestamp (via chai) as: 2020-01-30T02:54:48Z [192.168.1.200]
token.TokenService {390782} tokenPayload={"issueTime":"2020-01-31T18:06:38Z","name":"ACTIVATION","guid":"0364437a-9999-4849-8245-750062dd1383","expiration":"2020-01-31T18:11:38Z","user":"cn=TestUser,ou=users,o=data (default)"}, sessionUser=null, payloadUserIdentity=cn=TestUser,ou=users,o=data (default), userLastPasswordChange=2020-01-30T02:54:48Z, dateStringInToken=2020-01-30T02:54:48Z [192.168.1.200]
token.TokenService {390782} token validation has been passed [192.168.1.200]
token.TokenService {390782} removing claimed token: {"issueTime":"2020-01-31T18:06:38Z","name":"ACTIVATION","guid":"0364437a-9999-4849-8245-750062dd1383","expiration":"2020-01-31T18:11:38Z","user":"cn=TestUser,ou=users,o=data (default)"} [192.168.1.200]
Second token claim:
http.PwmResponse {390779} forwarding to /WEB-INF/jsp/activateuser-entercode.jsp [10.132.10.109]
http.PwmRequest {390779} GET request for: /sspr/public/activate (no params) completed requestID=2133810 in 2452ms [10.132.10.109]
http.PwmRequest {390779} POST request for: /sspr/public/activate requestID=2133827 [10.132.10.109]
token.TokenService {390779} 5037 ERROR_TOKEN_INCORRECT (token not found) [10.132.10.109]
http.PwmResponse {390779} forwarding to /WEB-INF/jsp/activateuser-entercode.jsp [10.132.10.109]
http.PwmRequest {390779} GET request for: /sspr/public/activate (no params) completed requestID=2133810 in 2452ms [10.132.10.109]
http.PwmRequest {390779} POST request for: /sspr/public/activate requestID=2133827 [10.132.10.109]
token.TokenService {390779} 5037 ERROR_TOKEN_INCORRECT (token not found) [10.132.10.109]
Note the IP address for each host claiming the token is different. The first IP address is the address of the outbound email scanner as it processed the link contained in the email. The second IP address is the address of the user workstation attempting to claim the token.