Environment
Reflection for the Web 2014 (All Editions)
Reflection for the Web 2011 (All Editions)
Situation
Resolution
Overview
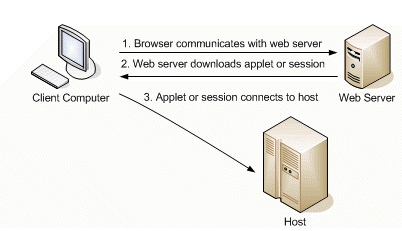
Reflection for the Web or Reflection Security Gateway uses a three-step process to connect to a host.
- The client computer uses a browser to communicate with the web server.
- The web server downloads the Reflection for the Web applet or session configuration to the client.
- The Reflection for the Web applet or session connects to the host.
With this basic understanding of how Reflection for the Web and Reflection Security Gateway make host connections, it is easier to understand why specific ports must be opened when you add a firewall to the environment.
There are many ways to incorporate Reflection for the Web or Reflection Security Gateway into a network environment with a firewall. The four scenarios described below are simple scenarios designed to illustrate the concept of opening ports to allow Reflection for the Web to communicate with the host. The examples provided may or may not reflect your environment.
Scenario TwoâReflection Security Proxy server
Scenario ThreeâReflection Security Proxy server using common port
Scenario FourâDirect, secure host connection
Scenario OneâNo security to host
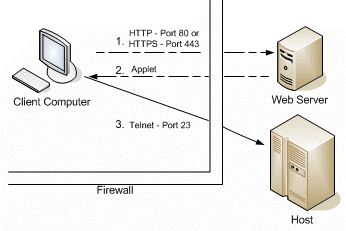
Scenario One depicts an example of connecting through a firewall if no security is used with the host. The communication between the client and the host is not encrypted. If you require a secure environment, this scenario is not recommended.
- Using a browser, the client computer communicates with the web server over HTTP (typically port 80, not encrypted) or over HTTPS (typically port 443, encrypted).
- The web server downloads the Reflection for the Web applet, or session configuration if using Reflection Security Gateway, to the client computer.
- The Reflection for the Web applet or session configuration connects to the host through the firewall over a protocol that the host supports. For example, the applet may connect Telnet (not encrypted) over port 23. The host computer must be accessible from outside the firewall.
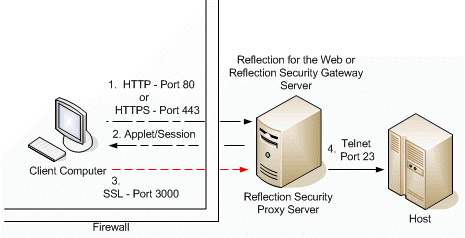
Scenario TwoâReflection Security Proxy server
In this scenario, the Reflection Security Proxy server is added. Communication between the client and the Reflection Security Proxy server is encrypted.
Note: Beginning in Reflection for the Web 2014, the security proxy server is not included in the Limited Edition. Beginning in Reflection for the Web 2008, the security proxy server is not included in the Standard Edition.
- Using a browser, the client computer communicates with the web server over HTTP (typically port 80, not encrypted) or over HTTPS (typically port 443, encrypted).
- The web server serves the Reflection for the Web applet, or session configuration if using Reflection Security Gateway, to the client computer.
- The Reflection for the Web applet or session configuration on the client computer connects to the Reflection Security Proxy server through the firewall using a preconfigured port, in this example, port 3000.
The Reflection Security Proxy server must be accessible from outside the firewall. The communication between the client applet and the security proxy is encrypted (Telnet encrypted with SSL).
- The Reflection Security Proxy server decrypts the packets and forwards them to the host over Telnet (not encrypted) over port 23.
See KB 7022328 for information about configuring the Reflection Security Proxy server in a Windows environment.
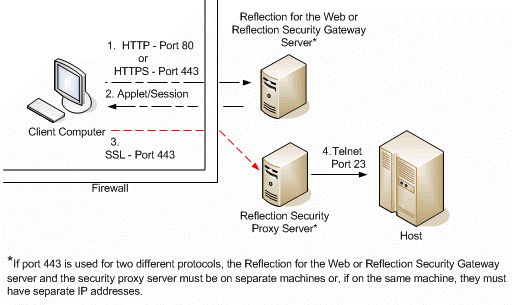
Scenario ThreeâReflection Security Proxy server using common port
To reduce the number of ports open in your firewall, you may want to use a common port for traffic going to the Reflection Security Proxy server. For example, if port 443 is already open for HTTPS traffic, you may want to configure the security proxy to use this port also. In this scenario, the client is connecting to the host through the firewall via the Reflection Security Proxy server. This scenario assumes that the client uses HTTP (port 80) or HTTPS (port 443) to connect to the web server, and uses SSL over port 443 to connect to the Reflection Security Proxy server.
Note: Beginning in Reflection for the Web 2014, the Reflection Security Proxy server is not included in the Limited Edition. Beginning in Reflection for the Web 2008, the Reflection Security Proxy server is not included in the Standard Edition.
- The client computer connects to the Reflection for the Web or Reflection Security Gateway server over port 80 if using HTTP (not encrypted) or over port 443 if using HTTPS (encrypted).
- The web server serves the Reflection for the Web applet, or session configuration if using Reflection Security Gateway, to the client computer.
- The Reflection for the Web applet or session configuration on the client computer connects to the Reflection Security Proxy server through the firewall over SSL using port 443. The Reflection Security Proxy server must be accessible from outside the firewall.
- The Reflection Security Proxy server decrypts the packets and forwards them to the host over Telnet (not encrypted) using port 23.
Note: If you are using an HTTP/HTTPS stateful filtering firewall (such as DMZ/Shield), it may be incompatible with the proxy server because the protocol in the SSL pipe is Telnet and not HTTP.
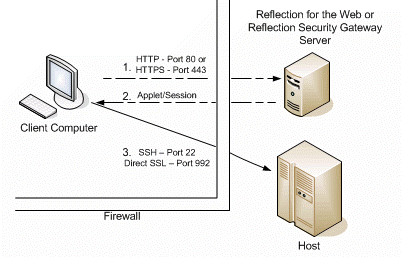
Scenario FourâDirect, secure host connection
This scenario illustrates a session between the client and host through a firewall in which the data is encrypted both inside and outside the firewall. This scenario requires the host computer to have either an SSL-encrypted Telnet server or an SSH server installed and configured.
- The client computer connects to the Reflection for the Web or Reflection Security Gateway server over port 80 if using HTTP (not encrypted) or over port 443 if using HTTPS (encrypted).
- The Reflection for the Web server serves the Reflection for the Web applet, or session configuration if using Reflection Security Gateway, to the client computer.
- The Reflection for the Web applet or session configuration on the client computer connects to the host through the firewall by using either Secure Shell (encrypted) typically over port 22 or direct SSL (encrypted) typically over port 992.
For more information about configuring Reflection for the Web to use Secure Shell, see KB 7022043. Additional information about configuring Reflection for the Web to use SSL is contained in Technical Note 1759 and KB 7022182.