Environment
Reflection Pro 2014 R1
Reflection X 2014 R1
Reflection for UNIX and OpenVMS 2014 R1
Reflection for IBM 2014 R1
Reflection for UNIX and OpenVMS version 14.1 SP3
Reflection for IBM version 14.1 SP3
Reflection for HP with NS/VT version 14.1 SP3
Reflection FTP Client version 14.1 SP3 and 15.6
Situation
The application versions listed above support TLS 1.2 connections. These application versions are vulnerable to the OpenSSL 'Heartbleed' vulnerability (CVE-2014-0160) only if TLS version 1.2 has been enabled. This technical note describes how to determine if your connections use TLS version 1.2.
Notes:
- Earlier versions than those listed in the Applies To section do not support TLS 1.2 and are not vulnerable.
- None of these applications use TLS 1.2 by default. The default Reflection 2014 R1 and 14.1 SP3 TLS 1.0 connections are not subject to this vulnerability because Attachmate TLS 1.0 connections use a non-vulnerable OpenSSL version.
- If you do require TLS 1.2 for any connections, see KB 7021974 for additional information about the vulnerability and how to obtain updates to fix your product.
Resolution
Viewing the SSL/TLS Settings
Security settings are configurable for each connection separately. To ensure that none of your connections use TLS 1.2, repeat this check for each configured connection.
- Open the Security Properties dialog box.
The procedure for opening this box depends on which product you use. See How to Open the Security Properties Dialog Box.
- Click the SSL/TLS tab.
- If "Use SSL/TLS security" is unchecked, this connection does not use SSL/TLS and is not vulnerable.
- If "Use SSL/TLS security" is selected, look at the SSL/TLS version setting. The connection is vulnerable only if TLS Version 1.2 is selected. (TLS Version 1.0 and SSL Version 3.0 are not vulnerable.)
View Full Size
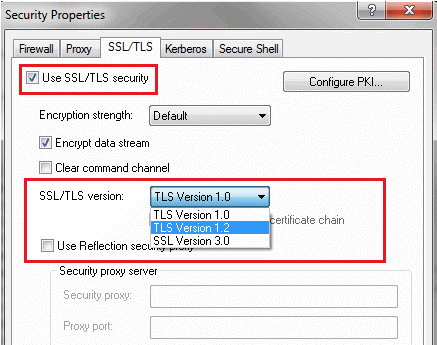
Only TLS Version 1.2 connections are vulnerable
How to Open the Security Properties Dialog Box
The procedure for opening this box depends on which product you use:
Reflection 2014 Workspace
Reflection for UNIX and OpenVMS 14.1
Reflection for HP 14.1
Reflection for IBM 14.1
FTP Client
The FTP Client is included with all of the products listed above. To open the Security Properties dialog box from the FTP Client:
- Start the FTP Client. The "Connect to FTP Site" dialog box opens automatically. Or, if the FTP Client is already running, go to Connection > Connect to open this dialog box.
- Select the site you want to check and click Security.
Reflection 2014 Workspace
To open the Security Properties dialog box from the Reflection Workspace:
- Select the connection you want to check.
- From the Quick Access Toolbar, click the Document Settings icon.
- Open the security settings for your connection type:
For VT Sessions
- Under Host Connection, click Configure Connection Settings.
- If either Secure Shell or Rlogin is selected, your connection does not use SSL/TLS.
- If Telnet is selected, click Security to open the Security Properties dialog box.
For 3270 and 5250 sessions, only
- Under Host Connection, click Set up Connection Security.
- Click Security Settings.
Reflection for UNIX and OpenVMS 14.1
Reflection for HP 14.1
To open the Security Properties dialog box from Reflection for UNIX and OpenVMS 14.1, or Reflection for HP 14.1.
- Open the settings file you want to check.
- Go to Connection > Connection Setup.
- Look under "Connect Using."
- If Network is set to Telnet, click Security to open the Security Properties dialog box.
- If any other Network setting is configured, your connection does not use SSL/TLS.
Reflection for IBM 14.1
To open the Security Properties dialog box from Reflection for IBM:
- Open the settings file you want to check.
- Go to Connection > Session Setup.
- Look under Transport.
- If the Transport Type is set to Telnet or Telnet Extended, click Security to open the Security Properties dialog box.
- If any other transport type is configured, your connection does not use SSL/TLS.