Environment
eDirectory 9
iManager 3
Certificate Server Plugin 9.0.3.20170613
iManager 3
Certificate Server Plugin 9.0.3.20170613
Situation
The CRL Configuration object for RSA certificates in the tree had its distribution points modified by removing those that were present and creating a new one with the iManager Certificate Server plugin. While the older certificates still successfully validate, any new ones result in a CRL decode error.
Resolution
There is a problem with the Certificate Server plugin. The plugin is inserting hard coded values into the distribution points on the CRL configuration object. Using the main eDirectory object modify task these values can be manually corrected.
Additional Information
A. Check references
Before checking the distribution point URLs there are 3 important object references to verify. All must be correct for the CRL portion of certificate validation to occur.
1. Config Object --> DN of CA
Confiiguration Object is linked to the RootCA.
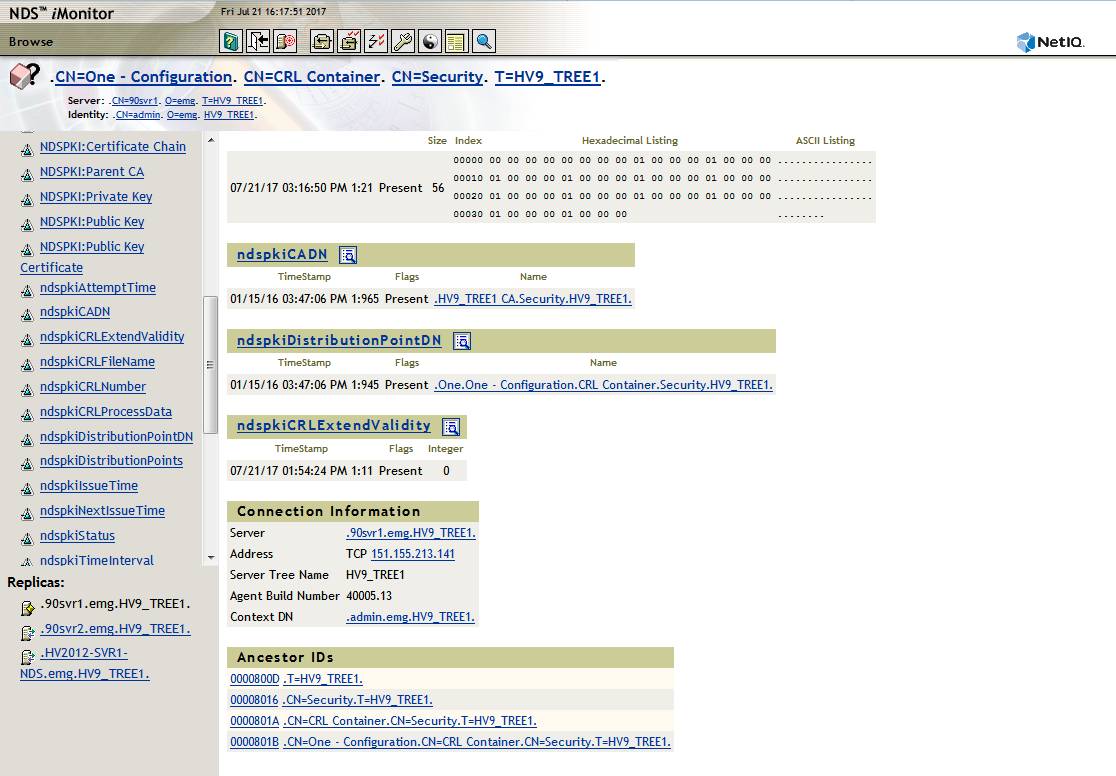
Here the CRL Configuration object is displayed in iMonitor: CN=One - Configuration. CN=CRL Container. CN=Security. T=HV9_TREE1.
This object's ndspkiCADN attribute value is properly pointing to the Tree's CA: HV9_TREE1 CA.Security.HV9_TREE1.
2. CA --> CRL Configuration Object
RootCA is linked back to the CRL Confiiguration Object
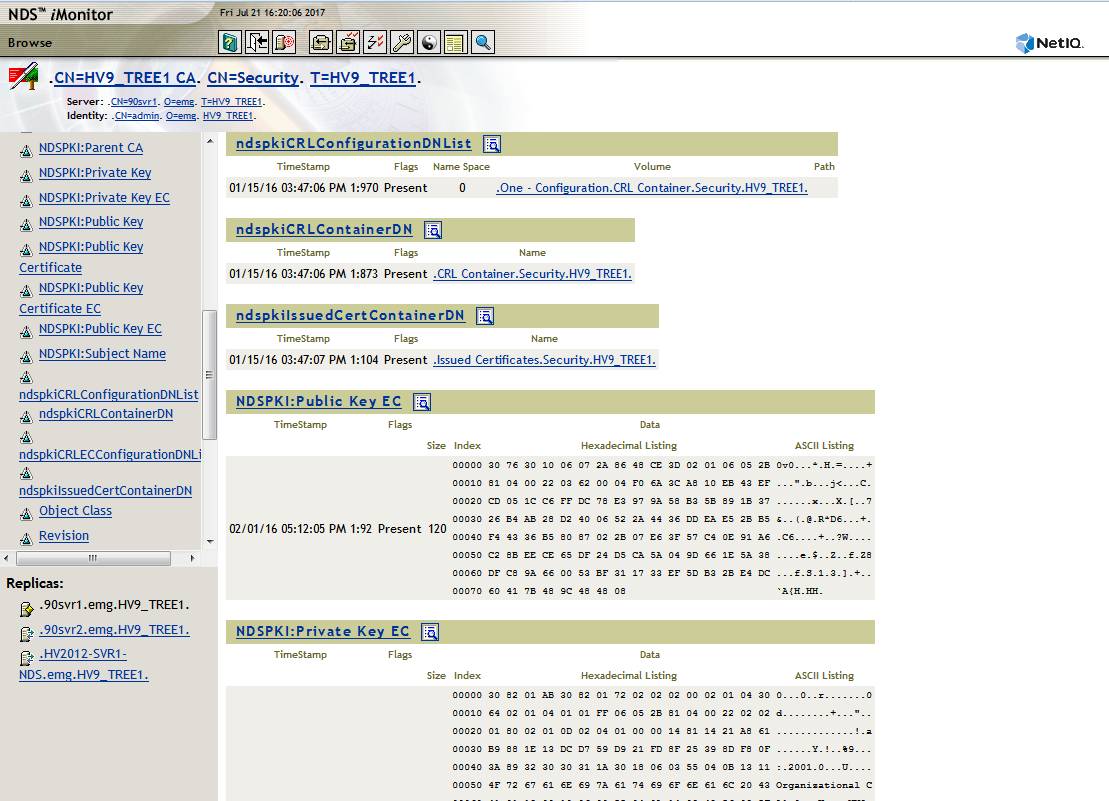
Here the RootCA object is displayed in iMonitor: CN=HV9_TREE1 CA. CN=Security. T=HV9_TREE1.
This object's attribute value ndspkiCRLConfigurationDNList is properly pointing to the Tree's CRL configuration object: One - Configuration.CRL Container.Security.HV9_TREE1.
3. CRL Configuration Object --> Distribution Point DN
The CRL Configuration Object must correctly point to the Distribution Point object
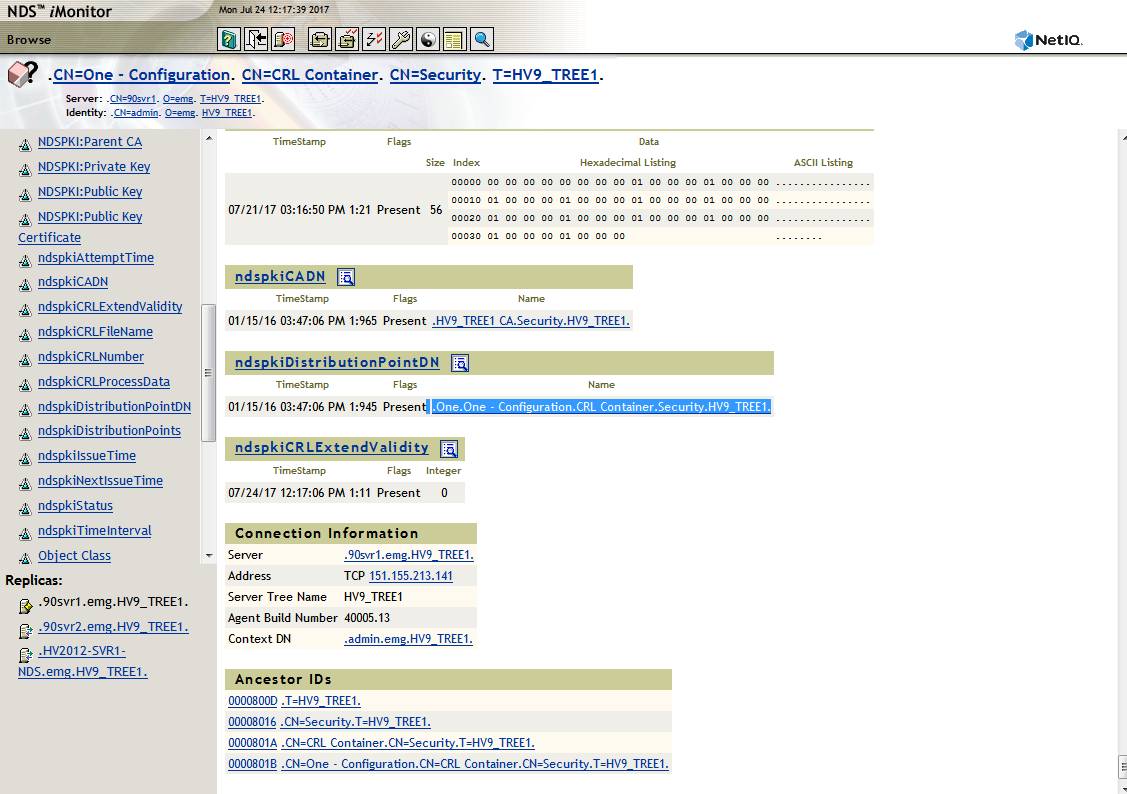
The third reference to verify is the ndspkiDistributionPointDN attribute on the CRL Configuration object correctly points to the correct Distribution Point object, in this case One.One - Configuration.CRL Container.Security.HV9_TREE1.
B. Verify Distribution Point URLs on Config Object
The following must all be true:
A. The CRL configuration object must have the correct CRL URLs
B. The URLs must be reachable from clients
C. DNS must be properly configured for the server hosting the CRL file.
D. The proper path and file name must be present in the Configuration object's ndspkiCRLFileName attribute.
This is easiest to verify in iManager but iMonitor could be used as well. Once logged into iManager navigate to:
NetIQ Certificate Server - Configure Certificate Authority - CRL tab - click on appropriate Distribution Object. In this example it is One.One - Configuration.CRL Container.Security.HV9_TREE1.
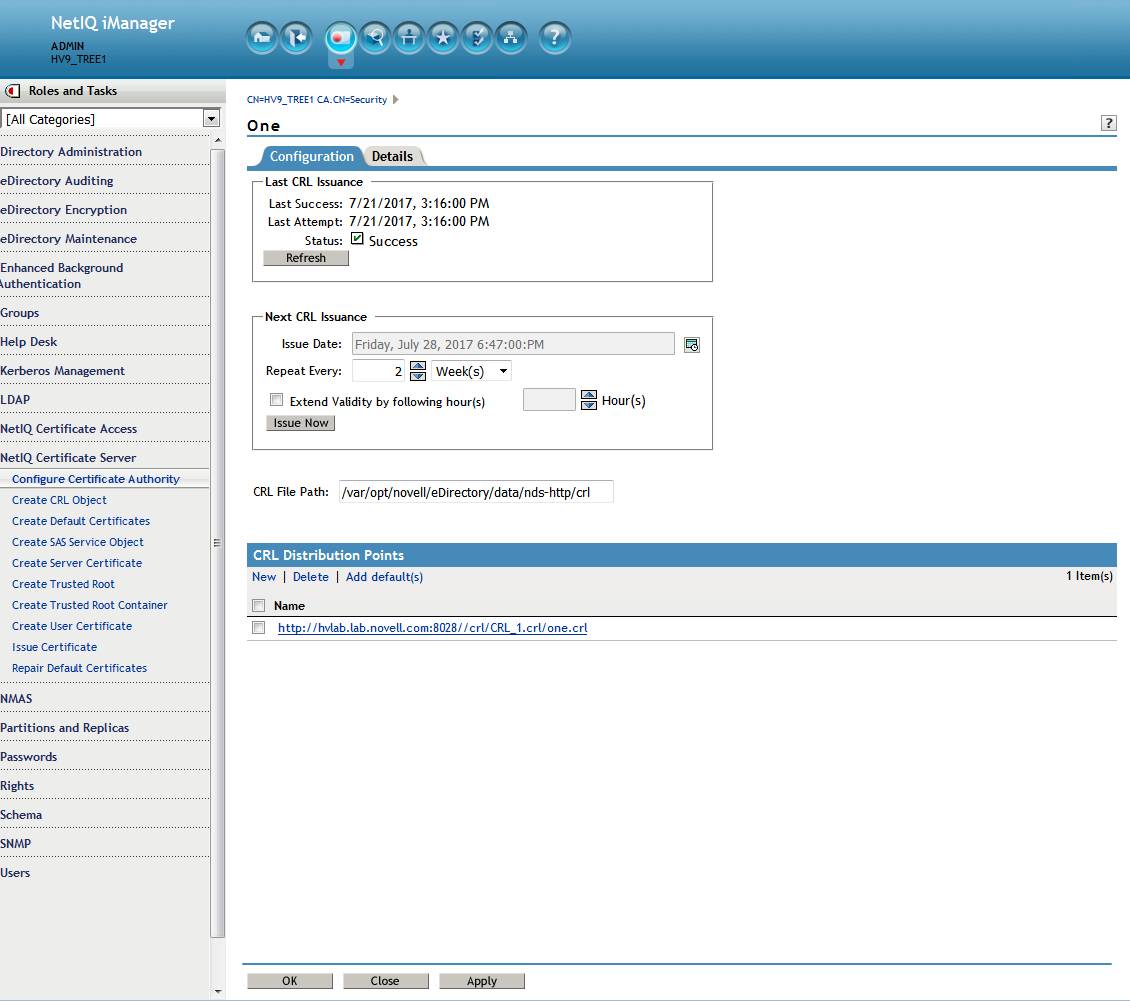
Here we see multiple problems. The CRL file path does not match the URL. A custom path and file name was selected. However, the plugin is expecting certain values so is incorrectly adding them.
- there is an extra backslash after the port number. A leading forward slash was incorrectly not escaped by the plugin when originally creating the distribution point.
- the file name one.crl was incorrectly appended by the plugin which breaks the path.
- Note: note that standalone eDirectory does not listen on port 80 by default. Its unsecure HTTP port is 8028. In this case that is correct.
- DNS: Also verify that unless another server is hosting the CRL file the RootCA server's FQDN name should be used. In this case that is also correct.
This can be easily corrected outside of the Certificate Server plugin in iManager (which is the cause of the problem). In the above example the path and file name will be corrected to use the default one.
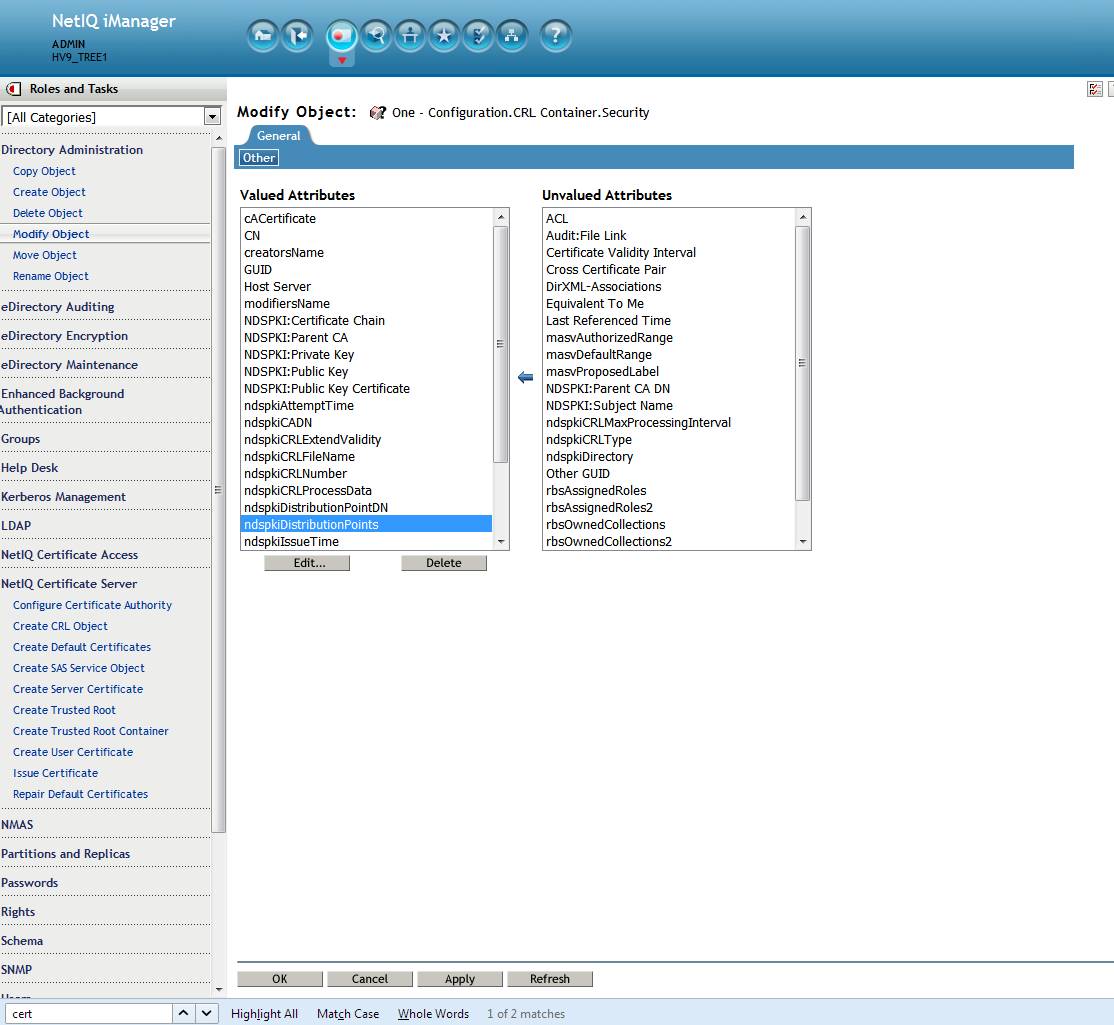
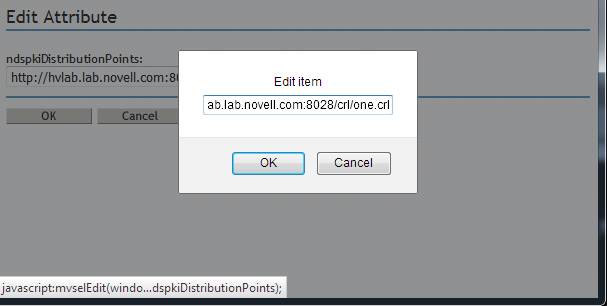
After logging into iManager navigate to Directory Administration - Modify Object - select the appropriate CRL Configuration object. In this case it is One - Configuration.CRL Container.Security. Now the General - Other tab is displayed for the object. Select the ndspkiDistributionPoints attribute. Click on edit. The edit Attribute page is displayed. In this case it is: http://hvlab.lab.novell.com:8028//crl/CRL_1.crl/one.crl. This will be corrected to read http://hvlab.lab.novell.com:8028/crl/one.crl. Do so by clicking on the pencil icon and correcting the text. The click on Ok - Apply - Ok.
Create a new server certificate. The certificate should now verify in iManager using the Certificate Server plugin. If not, use the Certificate Server plugin to force a re-issuance of the CRL file to the file system.
Note: any certificates created with the bad URLs will need to be recreated.
Before checking the distribution point URLs there are 3 important object references to verify. All must be correct for the CRL portion of certificate validation to occur.
1. Config Object --> DN of CA
Confiiguration Object is linked to the RootCA.

Here the CRL Configuration object is displayed in iMonitor: CN=One - Configuration. CN=CRL Container. CN=Security. T=HV9_TREE1.
This object's ndspkiCADN attribute value is properly pointing to the Tree's CA: HV9_TREE1 CA.Security.HV9_TREE1.
2. CA --> CRL Configuration Object
RootCA is linked back to the CRL Confiiguration Object

Here the RootCA object is displayed in iMonitor: CN=HV9_TREE1 CA. CN=Security. T=HV9_TREE1.
This object's attribute value ndspkiCRLConfigurationDNList is properly pointing to the Tree's CRL configuration object: One - Configuration.CRL Container.Security.HV9_TREE1.
3. CRL Configuration Object --> Distribution Point DN
The CRL Configuration Object must correctly point to the Distribution Point object

The third reference to verify is the ndspkiDistributionPointDN attribute on the CRL Configuration object correctly points to the correct Distribution Point object, in this case One.One - Configuration.CRL Container.Security.HV9_TREE1.
B. Verify Distribution Point URLs on Config Object
The following must all be true:
A. The CRL configuration object must have the correct CRL URLs
B. The URLs must be reachable from clients
C. DNS must be properly configured for the server hosting the CRL file.
D. The proper path and file name must be present in the Configuration object's ndspkiCRLFileName attribute.
This is easiest to verify in iManager but iMonitor could be used as well. Once logged into iManager navigate to:
NetIQ Certificate Server - Configure Certificate Authority - CRL tab - click on appropriate Distribution Object. In this example it is One.One - Configuration.CRL Container.Security.HV9_TREE1.

Here we see multiple problems. The CRL file path does not match the URL. A custom path and file name was selected. However, the plugin is expecting certain values so is incorrectly adding them.
- there is an extra backslash after the port number. A leading forward slash was incorrectly not escaped by the plugin when originally creating the distribution point.
- the file name one.crl was incorrectly appended by the plugin which breaks the path.
- Note: note that standalone eDirectory does not listen on port 80 by default. Its unsecure HTTP port is 8028. In this case that is correct.
- DNS: Also verify that unless another server is hosting the CRL file the RootCA server's FQDN name should be used. In this case that is also correct.
This can be easily corrected outside of the Certificate Server plugin in iManager (which is the cause of the problem). In the above example the path and file name will be corrected to use the default one.
After logging into iManager navigate to Directory Administration - Modify Object - select the appropriate CRL Configuration object. In this case it is One - Configuration.CRL Container.Security. Now the General - Other tab is displayed for the object. Select the ndspkiDistributionPoints attribute. Click on edit. The edit Attribute page is displayed. In this case it is: http://hvlab.lab.novell.com:8028//crl/CRL_1.crl/one.crl. This will be corrected to read http://hvlab.lab.novell.com:8028/crl/one.crl. Do so by clicking on the pencil icon and correcting the text. The click on Ok - Apply - Ok.


Create a new server certificate. The certificate should now verify in iManager using the Certificate Server plugin. If not, use the Certificate Server plugin to force a re-issuance of the CRL file to the file system.
Note: any certificates created with the bad URLs will need to be recreated.