Environment
Self Service Passwored Reset
SSPR 3.3
SSPR 3.3
Situation
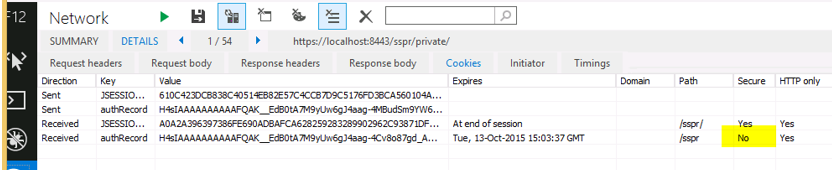
"authRecord" cookie sent by SSPR shows as not secure
F12 developer tools and Webinspector list authRecord cookie as not secure
What is the authRecord cookie used by SSPR and what does it do?
F12 developer tools and Webinspector list authRecord cookie as not secure
What is the authRecord cookie used by SSPR and what does it do?

Resolution
There is not a way to set the cookie's secure
flag, but you can configure SSPR to either ignore the cookie, or to not send it.
To ignore this cookie set "previous authentication" to "Not Used" in Modules --> Forgotten Password --> Forgotten Password Profile --> <profile> --> Verification Methods.
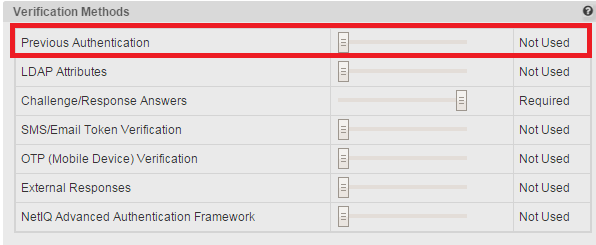
The auth record cookie is used to indicate if a user has logged in previously. It is only used if "Verification Methods" for the forgotten password module include "previous authentication." This cookie will not be read by SSPR unless "previous authentication" is set to required or optional.
To prevent this cookie from being sent at all, enter http.cookie.authRecord.name in Configuration Manager --> Settings --> Application --> App Property Overrides as shown below:
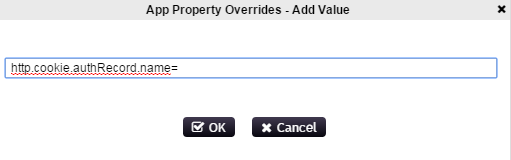
Note: "App Property Overrides" was made available beginning with SSPR 3.3. For SSPR 3.2 you can prevent this cookie from being sent by manually modifying SSPRConfiguration.xml and adding:
<property key="http.cookie.authRecord.name"> </property>
CAUTION: Only use "App Property Overrides" when directed by MicroFocus Customer Care. The values to be entered may change from version to version and should be confirmed. The setting documented in this article pertains to SSPR 3.3.
To ignore this cookie set "previous authentication" to "Not Used" in Modules --> Forgotten Password --> Forgotten Password Profile --> <profile> --> Verification Methods.

The auth record cookie is used to indicate if a user has logged in previously. It is only used if "Verification Methods" for the forgotten password module include "previous authentication." This cookie will not be read by SSPR unless "previous authentication" is set to required or optional.
To prevent this cookie from being sent at all, enter http.cookie.authRecord.name in Configuration Manager --> Settings --> Application --> App Property Overrides as shown below:

Note: "App Property Overrides" was made available beginning with SSPR 3.3. For SSPR 3.2 you can prevent this cookie from being sent by manually modifying SSPRConfiguration.xml and adding:
<property key="http.cookie.authRecord.name"> </property>
CAUTION: Only use "App Property Overrides" when directed by MicroFocus Customer Care. The values to be entered may change from version to version and should be confirmed. The setting documented in this article pertains to SSPR 3.3.
Additional Information
The idea of 'secure' cookies can be a bit misleading. The 'secure' flag on a cookie prevents the cookie from being sent over
unsecure (http) channels. If the channel is secure (https) then the
cookie is also secure. The flag is an extra safegaurd in case the channel
is unexpectedly not secure.