Environment
NetIQ Privileged User Manager
Situation
SSH relay sessions auditing reveals privileged user password.
The password that SSH relay uses for authenticating to the remote system is shown in the PUM Audit logs. This is a potential security breach since it gives the person viewing audit logs access to a privileged password.
Resolution
The likely cause of this is that the Audit Settings in the Command Control page does NOT have the password filter set. The attached screenshots show both the Audit Settings link, and the basic configuration of the password filter:
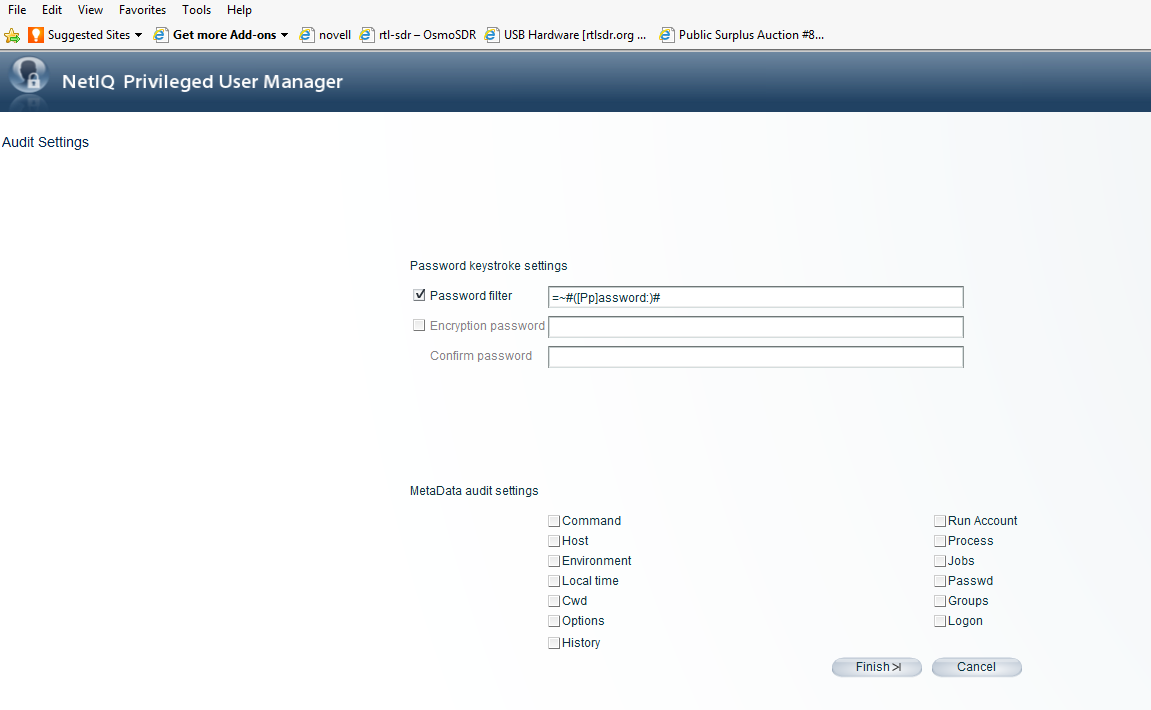
The next screenshot shows the password filter both enabled, and configured with =~#([Pp]assword:)# as the string to filter on, this will grab password: spelled with either an uppercase or a lowercase letter p. NOTE: The filter is used when writing the data to the log. Also, if the 'Encryption Password' is set, the password will be encrypted before being written to the log, and the 'Encryption Password' would be used to decrypt it, in case it were ever necessary to audit what password was being attempted.