Environment
Novell Client 2 SP2 for Windows
Novell Client 2 SP3 for Windows
Novell Client 2 SP3 for Windows
Novell Client 2 SP4 for Windows
Windows 7 (x86 or x64) (Ultimate Edition, Enterprise Edition, or Professional Edition)
Windows Vista (x86 or x64) (Ultimate Edition, Enterprise Edition, or Business Edition)
Windows Server 2008 R2 (x64) (Enterprise Edition, or Standard Edition)
Windows Server 2008 (x86 or x64) (Enterprise Edition, or Standard Edition)
Windows Server 2012 (x64)
Windows 7 (x86 or x64) (Ultimate Edition, Enterprise Edition, or Professional Edition)
Windows Vista (x86 or x64) (Ultimate Edition, Enterprise Edition, or Business Edition)
Windows Server 2008 R2 (x64) (Enterprise Edition, or Standard Edition)
Windows Server 2008 (x86 or x64) (Enterprise Edition, or Standard Edition)
Windows Server 2012 (x64)
Situation
How will an expiring certificate affect my use of the Novell Client? Specifically, what happens with existing Clients when the certificate expires and, can the Client still be installed once the certificate has already expired?
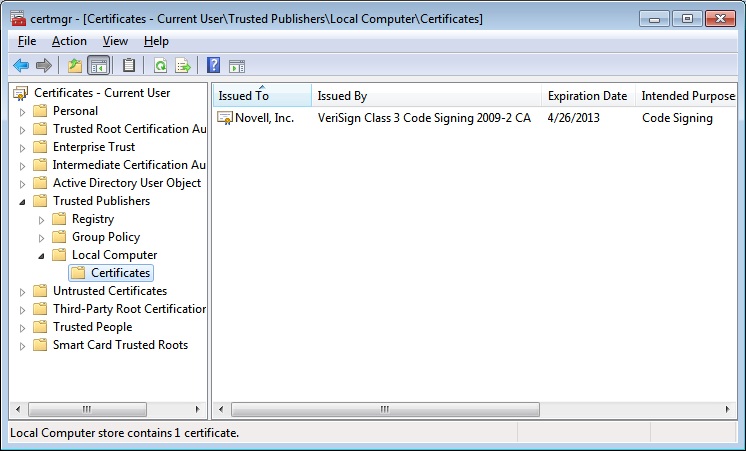
Assuming the certificate has been installed in the local certificate store (either interactively when prompted to approve installation (via the "Always trust software from Novell,
Inc." checkbox), or by an administrator pre-installing the certificate to the
Microsoft "Trusted Publishers" certificate store before the Novell Client
software installation occurs), the certificate details can be viewed in Microsoft Management Console (mmc.exe) as in this example:
Resolution
Nothing will happen to an existing installed Novell Client for Windows on or after the expiration date of the certificate. Windows will continue to be able to verify the signatures applied to the binaries (on the platform where binary signatures are enforced) due to presence of the time stamp signature which was also applied to the files. Windows will continue to conclude that the file is validly signed, because the certificate was valid at the time the signature and time stamp were generated.
For example, a Novell Client for Windows installation set that uses the June 3, 2016 certificate can continue to be installed and used after June 3, 2016 Windows will continue to be able to verify the signatures applied to the installation set due to presence of the time stamp signature which was also applied to the files. Windows will continue to conclude that the installation set is validly signed, because the certificate was valid at the time the signature and time stamp were generated.
For example, a Novell Client for Windows installation set that uses the June 3, 2016 certificate can continue to be installed and used after June 3, 2016 Windows will continue to be able to verify the signatures applied to the installation set due to presence of the time stamp signature which was also applied to the files. Windows will continue to conclude that the installation set is validly signed, because the certificate was valid at the time the signature and time stamp were generated.
NOTE:
Beginning with Client for Open Enterprise Server 2 SP4 (IR3), the Client includes an SHA-2 Micro Focus certificate instead of SHA-1 Novell, Inc. certificate. This certificate is valid until 1 Aug 2018. See TID 7017719 for a related issue.
Additional Information
The online documentation for the Novell Client 3 SP3 for Windows states:
"For the Novell Client, the certificate used for Authenticode signing is the Verisign* public certificate for Novell, Inc. The best way to obtain the correct certificate for use in the Trusted Publishers list is to install the Novell Client on a Windows machine, then select the Always trust software from Novell, Inc. option when prompted."
It goes on to state:
"For the Novell Client, the certificate used for Authenticode signing is the Verisign* public certificate for Novell, Inc. The best way to obtain the correct certificate for use in the Trusted Publishers list is to install the Novell Client on a Windows machine, then select the Always trust software from Novell, Inc. option when prompted."
It goes on to state:
"Certificates have an expiration date, and the certificate a software publisher uses will eventually change as the current certificate reaches expiration and a renewed certificate is obtained. For example, the certificate currently used to sign the Novell Client 2 SP1 for Windows is valid until 2013, so pre-distributing this certificate will work for future Novell Client software releases until the year 2013."
Expiration of the Novell certificate used to sign released versions of the Novell Client is not expected to affect installation or use of those released Novell Client software products, because the signature is also time stamped as a separate additional step in the signing process. Via the signature time stamp, Windows Authenticode and other verifiers of the signature wrapper are able to prove and conclude "the signature was valid and non-expired at the time this software was actually signed".
Without the time stamp signature having been applied in addition to the code signing signature itself, indeed these same binaries and installation set packages would have otherwise started failing their signature verification after the certificate expiration date. But that will not be the case, since these binaries and installation set packages have also been time stamped during the signing process.
Any updated certificate intends to pick up where the existing certificate expiration period ends. The updated certificate is expected to be available as an integral part of the next Novell Client for Windows build that is published after the certificate expires.
Customers who wish to pre-publish that certificate as a Trusted Publisher certificate for Windows will be able to retrieve the updated public certificate from the signed code when it is released.
Additional information on Time Stamping Windows Authenticode Signatures is available at http://msdn.microsoft.com/en-us/library/bb931395(VS.85).aspx.
Expiration of the Novell certificate used to sign released versions of the Novell Client is not expected to affect installation or use of those released Novell Client software products, because the signature is also time stamped as a separate additional step in the signing process. Via the signature time stamp, Windows Authenticode and other verifiers of the signature wrapper are able to prove and conclude "the signature was valid and non-expired at the time this software was actually signed".
Without the time stamp signature having been applied in addition to the code signing signature itself, indeed these same binaries and installation set packages would have otherwise started failing their signature verification after the certificate expiration date. But that will not be the case, since these binaries and installation set packages have also been time stamped during the signing process.
Any updated certificate intends to pick up where the existing certificate expiration period ends. The updated certificate is expected to be available as an integral part of the next Novell Client for Windows build that is published after the certificate expires.
Customers who wish to pre-publish that certificate as a Trusted Publisher certificate for Windows will be able to retrieve the updated public certificate from the signed code when it is released.
Additional information on Time Stamping Windows Authenticode Signatures is available at http://msdn.microsoft.com/en-us/library/bb931395(VS.85).aspx.