Environment
Novell Open Enterprise Server 2 SP2 (OES 2SP2) Linux
Domain Services for Windows 1.1
DSFW 1.1
Upgrade from OeS2SP1 to OES2SP2
Domain Services for Windows 1.1
DSFW 1.1
Upgrade from OeS2SP1 to OES2SP2
Situation
After upgrading from OES2SP1 to OES2SP2 can not join workstations to the domain or manage the domain with MMC.
After enabling debug logging in SMB.CONF (log level =10) the /var/log/samba/log.smb shows the following when trying to connect to the domain with MMC
[[2009/12/03 12:17:51, 10] libads/kerberos_verify.c:ads_keytab_verify_ticket(126)
ads_keytab_verify_ticket: krb5_rd_req_return_keyblock_from_keytab(SERVER1$@DSFW.LOCAL) failed: Wrong principal in request
[2009/12/03 12:17:51, 10] libads/kerberos_verify.c:ads_keytab_verify_ticket(126)
ads_keytab_verify_ticket: krb5_rd_req_return_keyblock_from_keytab(SERVER1$@DSFW.LOCAL) failed: Wrong principal in request
[2009/12/03 12:17:51, 10] libads/kerberos_verify.c:ads_keytab_verify_ticket(126)
ads_keytab_verify_ticket: krb5_rd_req_return_keyblock_from_keytab(SERVER1$@DSFW.LOCAL) failed: Wrong principal in request
[2009/12/03 12:17:51, 10] libads/kerberos_verify.c:ads_keytab_verify_ticket(126)
ads_keytab_verify_ticket: krb5_rd_req_return_keyblock_from_keytab(host/server1.dsfw.local@DSFW.LOCAL) failed: Wrong principal in request
[2009/12/03 12:17:51, 10] libads/kerberos_verify.c:ads_keytab_verify_ticket(126)
ads_keytab_verify_ticket: krb5_rd_req_return_keyblock_from_keytab(host/server1.dsfw.local@DSFW.LOCAL) failed: Wrong principal in request
[2009/12/03 12:17:51, 3] libads/kerberos_verify.c:ads_keytab_verify_ticket(172)
ads_keytab_verify_ticket: krb5_rd_req failed for all 5 matched keytab principals
[2009/12/03 12:17:51, 1] libads/kerberos_verify.c:ads_secrets_verify_ticket(237)
ads_secrets_verify_ticket: failed to fetch machine password
[2009/12/03 12:17:51, 10] passdb/secrets.c:secrets_named_mutex_release(996)
secrets_named_mutex: released mutex for replay cache mutex
[2009/12/03 12:17:51, 3] libads/kerberos_verify.c:ads_verify_ticket(427)
ads_verify_ticket: krb5_rd_req with auth failed (Cannot read password)
[2009/12/03 12:17:51, 10] libads/kerberos_verify.c:ads_verify_ticket(436)
ads_verify_ticket: returning error NT_STATUS_LOGON_FAILURE
[2009/12/03 12:17:51, 1] smbd/sesssetup.c:reply_spnego_kerberos(316)
Failed to verify incoming ticket with error NT_STATUS_LOGON_FAILURE!
After enabling debug logging in SMB.CONF (log level =10) the /var/log/samba/log.smb shows the following when trying to connect to the domain with MMC
[[2009/12/03 12:17:51, 10] libads/kerberos_verify.c:ads_keytab_verify_ticket(126)
ads_keytab_verify_ticket: krb5_rd_req_return_keyblock_from_keytab(SERVER1$@DSFW.LOCAL) failed: Wrong principal in request
[2009/12/03 12:17:51, 10] libads/kerberos_verify.c:ads_keytab_verify_ticket(126)
ads_keytab_verify_ticket: krb5_rd_req_return_keyblock_from_keytab(SERVER1$@DSFW.LOCAL) failed: Wrong principal in request
[2009/12/03 12:17:51, 10] libads/kerberos_verify.c:ads_keytab_verify_ticket(126)
ads_keytab_verify_ticket: krb5_rd_req_return_keyblock_from_keytab(SERVER1$@DSFW.LOCAL) failed: Wrong principal in request
[2009/12/03 12:17:51, 10] libads/kerberos_verify.c:ads_keytab_verify_ticket(126)
ads_keytab_verify_ticket: krb5_rd_req_return_keyblock_from_keytab(host/server1.dsfw.local@DSFW.LOCAL) failed: Wrong principal in request
[2009/12/03 12:17:51, 10] libads/kerberos_verify.c:ads_keytab_verify_ticket(126)
ads_keytab_verify_ticket: krb5_rd_req_return_keyblock_from_keytab(host/server1.dsfw.local@DSFW.LOCAL) failed: Wrong principal in request
[2009/12/03 12:17:51, 3] libads/kerberos_verify.c:ads_keytab_verify_ticket(172)
ads_keytab_verify_ticket: krb5_rd_req failed for all 5 matched keytab principals
[2009/12/03 12:17:51, 1] libads/kerberos_verify.c:ads_secrets_verify_ticket(237)
ads_secrets_verify_ticket: failed to fetch machine password
[2009/12/03 12:17:51, 10] passdb/secrets.c:secrets_named_mutex_release(996)
secrets_named_mutex: released mutex for replay cache mutex
[2009/12/03 12:17:51, 3] libads/kerberos_verify.c:ads_verify_ticket(427)
ads_verify_ticket: krb5_rd_req with auth failed (Cannot read password)
[2009/12/03 12:17:51, 10] libads/kerberos_verify.c:ads_verify_ticket(436)
ads_verify_ticket: returning error NT_STATUS_LOGON_FAILURE
[2009/12/03 12:17:51, 1] smbd/sesssetup.c:reply_spnego_kerberos(316)
Failed to verify incoming ticket with error NT_STATUS_LOGON_FAILURE!
Resolution
Here are two known possibilities for the failure to join a domain after an upgrade.
1) The Domain Password Policy is not assigned to the Computers container or the Domain Controllers container.
Verify the Default Password Policy is assigned to the Computers container and Domain Controllers container. If not present, add the assignment. Edit the container and verify in the other tab that there is a nspmPasswordPolicyDN attribute. Add the nspmPasswordPolicyDN if it does not exist. If it exists verify the password policy assigned is the default Password Policy and make adjustments as necessary.
Below is an example viewing the password policy.
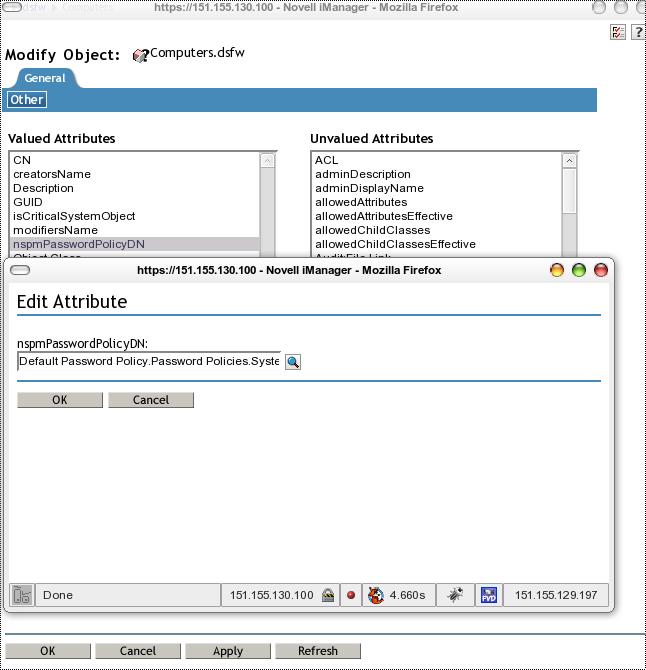
1) The Domain Password Policy is not assigned to the Computers container or the Domain Controllers container.
Verify the Default Password Policy is assigned to the Computers container and Domain Controllers container. If not present, add the assignment. Edit the container and verify in the other tab that there is a nspmPasswordPolicyDN attribute. Add the nspmPasswordPolicyDN if it does not exist. If it exists verify the password policy assigned is the default Password Policy and make adjustments as necessary.
Below is an example viewing the password policy.

2) The principal(s) is either incorrect in the keytab or the password for the domain controller account is not set.
The keytab needs to be renamed and a new one created while setting the domain controllers account password.
Below is an example of setting the password for a domain controller with shipping oes2sp2 named DOMAINSERVER. Changing the permissions, changing the group, and if a symbolic link is not created from the /etc to the keytab then creating a symbolic link to the krb5.keytab in the /etc folder.
/opt/novell/xad/sbin/setpassword -DNOSf -r -k /var/opt/novell/xad/ds/krb5kdc/krb5.keytab -u DOMAINSERVER$
chmod 640 /var/opt/novell/xad/ds/krb5kdc/krb5.keytab
chgrp named /var/opt/novell/xad/ds/krb5kdc/krb5.keytab
Verify there is a symbolic link at /etc/krb5.keytab to /var/opt/novell/xad/ds/krb5kdc/krb5.keytab. If not here is how to create the link
ln -s /var/opt/novell/xad/ds/krb5kdc/krb5.keytab /etc
For oes2sp2 or oes2sp3 with May maintenance patch or later the -E switch can be used to create mixed case principals.
/opt/novell/xad/sbin/setpassword -DNSOf -r -E DomainServer -k /var/opt/novell/xad/ds/krb5kdc/krb5.keytab -u DOMAINSERVER$
Example setting multiple mixed case names:
/opt/novell/xad/sbin/setpassword -DNSOf -r -E DomainServer,domainSERVER,DOMAINserver -k /var/opt/novell/xad/ds/kerb5kdc/krb5.keytab -u DOMAINSERVER$