Environment
Novell Identity Manager 3.x
NetIQ Identity Manager 4.x
Novell Identity Manager - Password Synchronization 2.0
Novell Identity Manager - Active Directory Driver
Situation
What are the Components Password Synchronization 2.0 uses when Synchronizing Passwords from Active Directory password changes to eDirectory? What are the corresponding Registry entries that Password Synchronization and its filters use?
Resolution
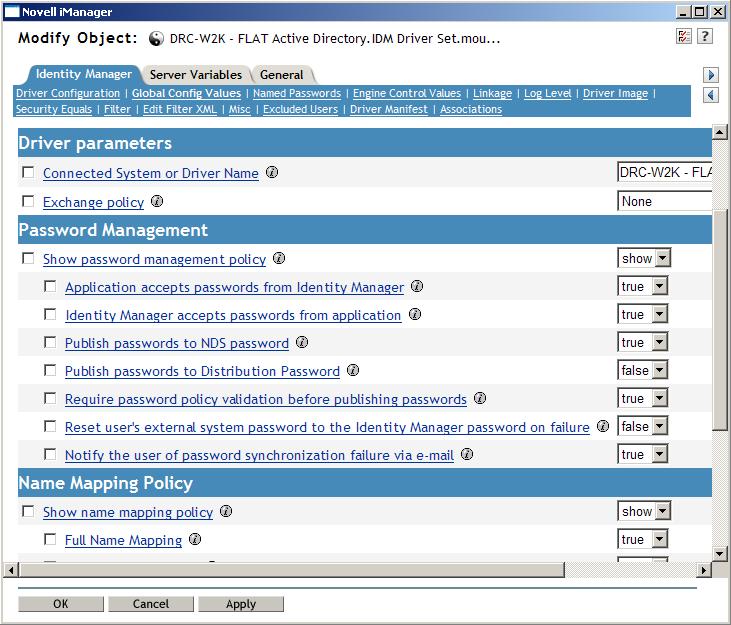
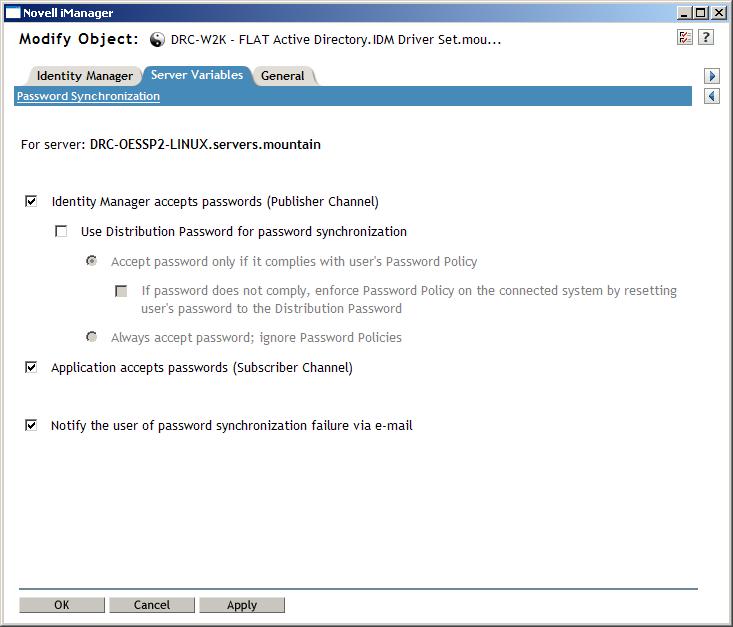
These are the components of Password Synchronization 2.0.
Files:
Note: The files listed below are all in the install media's nt/dirxml/system32 directory before IDM 3.5.x. As of IDM 3.5.x 64-bit Domain Controller (DC) support was added and as a result the pwfilter.dll and psevent.dll files are located in architecture-specific directories such as system32_dlls and system64_dlls.
PWFILTER.DLL - Main Password Sync application to capture Passwords. Placed in the directory defined by %SYSTEMDIRECTORY% (usually /windows/system32)
PSEVENT.DLL - Placed in the directory defined by %SYSTEMDIRECTORY%
PASSSYNCCONFIG.CPL - Password Sync Control Panel Applet. Placed in the directory defined by %SYSTEMDIRECTORY%
Registry Keys:
- HKLM/SOFTWARE/Novell/PassSync/
Driver Machine: REG_DWORD: 0x1 or 0x0
0x1 tells the passsyncconfig.cpl that this is where the driver (shim) is running
0x0 tells the passsyncconfig.cpl that the driver (shim) is not running on this machine.
- HKLM/SOFTWARE/Novell/PassSync/Data
Domains: REG_MULTI_SZ: This should be the DNS name of your domain
- HKLM/SOFTWARE/Novell/PassSync/Data/Enum Data: REG_BINARY : ....
Enum Index: REG_DWORD : ....
State: REG_DWORD : ....
- HKLM/SOFTWARE/Novell/PassSync/Data/<username>/
You will find entries of each user waiting for the password changes to flow from across the driver channel.
NOTE: Data's contents cannot normally be seen. Permissions in here are
limited to SYSTEM (Local System) only and are denied even to
Administrator. You must grant the user permissions to Data and below in order to see the keys.
- HKLM/SOFTWARE/Novell/PwFilter (32 Bit & 64 Bit)
- HKLM/SOFTWARE/Novell/PwFilter (32 Bit & 64 Bit)
Host Names: REG_MULTI_SZ:
This is the DNS name of the Domain Controller (DC) running the remote loader (or driver). The pwfilter.dll uses this key to know which server (driver shim) to send the password changes to synchronize over the channel. There SHOULD be only ONE server specified under this registry key. The server running the remote loader.
NOTE: Data's contents cannot normally be seen. Permissions in here are limited to SYSTEM (Local System) only and are denied even to Administrator. You must grant the user permissions to Data and below in order to see the keys.
- HKLM/SOFTWARE/Novell/PwFilter/Data/<username>/
The Password filter (on each domain controller) will pick up password changes and store them in a registry key for each user. It will then forward them to the machine running the remote loader (or driver).
- HKLM/SYSTEM/CurrentControlSet/Control/Lsa
Notification Packages: Reg_MULTI_Sz: PWFILTER
This notifies the pwfilter.dll of a password change.
Verify that the Driver is set to synchronize Passwords.
Global Config Values in the properties of the Driver.
Server Variables on the Properties of the Driver.
Flow of a password change - From Active Directory to eDirectory:
- Password is changed in AD by some means.
- Password change is picked up at a domain controller and pwfilter.dll is notified. (This is done by the fact that pwfilter is running and is a notification package in HKLM/SYSTEM/CurrentControlSet/Control/Lsa)
- PWFILTER places the password change in a new registry key under HKLM/SOFTWARE/Novell/PwFilter/Data/<username> for that user example: Password change for BOB1 would be in HKLM/SOFTWARE/Novell/PwFilter/Data/BOB1.
- The pwfilter.dll then sends the password change to the machine running the remote loader (or driver) (Determined by HKLM/SOFTWARE/Novell/PwFilter/Host Names:) and the password change is placed under the HKLM/SOFTWARE/Novell/PassSync/Data/<username>/ registry key on the remote loader (or driver) machine. This only occurs if the Remote loader is up and running and connected to the IDM Engine.
- The Remote Loader running the driver (shim) picks up the password change and sends it across the driver channel (as a normal XML document) to eDirectory in a password element. (Note: the Remote Loader will use the rights granted through the application username. If the user does not have rights to read the registry value for HKLM/SOFTWARE/Novell/PassSync/Data/ it will fail. )
- It follows the rules in the Active Directory driver and copies the password over to the nspmDistributionPassword attribute and then strips off the password element. After the the password is in the nspmDistributionPassword attribute in the XML document, it submits the password change to eDirectory where it is subject to the Universal Password policy assigned to the user. Depending upon the Universal Password policy rules defined, will sync to the NDS password and potentially the Simple Passwords and across to other connected systems.
Default Driver Behavior.
- The password is sent across as a password element from the Remote Loader to the Driver and through to eDirectory. It is not converted back to the nspmDistributionPassword attribute prior to setting the password.
- The password will not synchronize from AD to eDirectory if the user object is does not have an association. You will receive the error: Message: Code(-8019) Operation vetoed on unassociated object.
Note: When getting password sync traces for IDM, a Level 3 trace will show you the processing of policies and troubleshooting most password sync issues. A Level 5 trace on the remote loader trace, or driver trace, if the idm enginein is running on a Windows server, will give you more detail on password sync processing, which may be helpful at times.
BONUS: EDir to AD password sync (assumes the user is already associated).
- Password change is received.
- If User object has a Password Policy assigned to them and that password policy has Universal Password enabled and it is set to Synchronize Distribution Password when setting Universal Password, the password will be copied to the nspmDistributionPassword attribute on the user object.
- The password change will be captured by IDM and sent across the channel.
- Under the Command Transformation policy the rule 'Convert modifies of a nspmDistributionPassword attribute to a modify password operation' will copy password in the nspmDistributionPassword attribute over to a password element
- The password element is sent across the remote loader and updates the password through AD calls. (If you can update the password on the server running the remote loader with users and computers, the driver should be able to update the password.)
Additional Information
To get additional tracing detail of password synchronization, use a trace Level 5 on the the Remote Loader, if using a remote loader. Or Trace Level 5 on the Driver, if the IDM engine and eDirectory is running locally on the Windows server. You should see [PWD] tagged lines in the trace.
The most common issue with password sync from Active Directory to the Identity Vault are rights related issue. The application user being used for authentication in the driver must be sufficient rights to remotely read and write to the registry on each domain controller. Typically that means they need to be a member a of the Domain Admins and local Admins group on the DC. We commonly see group policies cause issues with these rights and cause access related errors or simply generate successful type returns (successful, in that nothing could be read, so nothing needs to be acted upon) in the password sync process. Carefully review all rights and restrictions being placed on the application user if you are having issues with password synchronization from Active Directory to the Identity Vault.