Environment
Novell SecureLogin version 3.5
Novell SecureLogin version 3.51
Novell SecureLogin version 3.51 SP1
Citrix
Microsoft Terminal Server
Situation
Resolution
Workstation components:
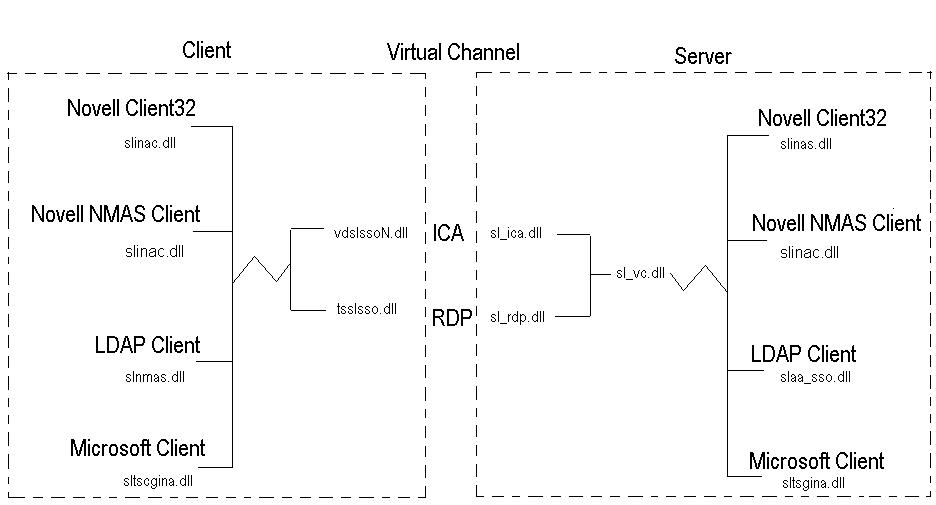
The workstation itself must be configured to capture the users credentials on login. This might be login to a Novell network, Microsoft network, or some other LDAP compliant network. In any case different modules are utilized to interface with the correct GINA (User Login Dialog) in each environment. This allows for the username, password, context, domain, etc. to be captured during the normal boot/login of the remote workstation. As seen in the chart below, this interface is supplied by the modules:
1. slinac.dll for Novell Client32
Each of these modules will capture the credentials from the cooresponding login dialog and store them in memory for access by SecureLogin. When SecureLogin loads it reads the encrypted values from memory and stores them in the ?sys variables. For example the username would be stored in the ?sysuser variable whereas the password would be stored in the ?syspassword variable. Of course these variables can be used in scripts for applications that utilize the same credentials. If for some reason the wrong module is being used or is missing, then when SecureLogin loads it will not be able to copy the values to the corresponding ?sys variable, and a script utilizing the ?sys variables will return a -426 error. Also, if passthrough authentication is configured and the variables are incorrect, then no credentials will be supplied to the Citrix session and a second login will be required. This is one of the most critical steps for the passthrough to complete successfully. Testing should be made to ensure that the credentials are captured correctly so that SecureLogin can supply them to either application scripts or passthrough authentication.
A quick way to validate this mechanism is working, is to create a notepad.exe script to echo the values to the application. Use the application wizard to create a basic application for notepad.exe. Then copy and paste over the notepad.exe script with the one below.
## BeginSection: "Test Notepad Script to display sys
variable"
Dialog
Class "Notepad"
Title "Untitled - Notepad"
EndDialog
Type \N
Type ?SYSUSER
Type \N
Type ?SYSPASSWORD
Type \N
## EndSection:
In addition to the components necessary to capture the users credentials from the initial login, SecureLogin needs a method of communicating that information between the users workstation environment and the actual Citrix session. This is done through the use of a virtual channel. SecureLogin works with 2 types of virtual channels in the Citrix environment. This would be ICA for a Citrix ICA session or RDP for a terminal server session. Two modules installed on the workstation allow the SecureLogin client to communicate with the specific virtual channel.
Server components:
Just like the client modules, different server modules are utilized depending on the environment. On the workstation we are concerned with the capturing of the credentials from the users initial login. But on the server side we are focused on taking those captured credentials and passing them through to the configured gina. The gina interface modules for the server are:
1. slinas.dll for Novell Client32
These modules again rely on the virtual channel to get the credentials from SecureLogin. The main interface module is sl_vc.dll that provides the interface to the virtual channel drivers. This module determines which of the two different virtual channels to query for the passthrough credentials. The two modules that actually provide the virtual channel are:
1. sl_ica.dll provides the virtual channel support within an ICA
session
1. User boots workstation. When prompted they enter their
credentials to login. The appropriate SecureLogin client interface
module captures these credentials, encrypts, and stores them in the
registry of the workstation.
Additional Information
Formerly known as TID# 10094565